Save to My DOJO
There have been many advancements in modern IT infrastructure. Virtualization has totally revolutionized the way that organizations view compute, storage, and networking. The notion of “virtualizing” the modern datacenter was a paradigm shift in many areas of IT infrastructure and datacenter technology. Workloads abstracted from the physical hardware have opened up tremendous efficiencies, and advantages in the way businesses can provide digital resources.
Along with server virtualization that allowed businesses to abstract running operating systems from the physical hardware, network virtualization has brought tremendous networking advantages. Much as they were in the area of server virtualization, VMware has been a pioneer in the area of network virtualization. VMware NSX is well-known in network virtualization and is a powerful solution that enables network virtualization, both in the data center, public cloud, and multi-cloud environments.
What challenges exist in data centers still leveraging traditional networking? What is VMware NSX? What is the difference between NSX-V and NSX-T? What advantages does NSX-T offer over NSX-V? What is the migration process to get from NSX-V to NSX-T? What features does NSX-T offer today to empower modern workloads?
Traditional data center networking challenges
VMware’s Software-Defined Data Center (SDDC) vision incorporates next-generation virtualization technologies. It allows organizations to realize automated, non-disruptive deployments of business-critical infrastructure in a way that helps reduce operational complexity and extend technical agility to deliver applications. By now, most organizations have virtualized most of their server infrastructure in their data centers and are also taking advantage of software-defined storage technologies.
Datacenter networks have historically been extremely slow to respond to the changing needs of the enterprise. Networking is often too rigid, complicated and presents many barriers to innovation and realizing the full potential of virtualizing other data center components such as servers and storage. Traditional networking technologies constrain the advantages gained by virtualizing servers and storage.
Traditional networking presents the following challenges:
- Provisioning new routers, switches, and other technologies is slow
- Proprietary networking technologies historically bind traditional networking from specific networking vendors
- Automated network configuration is generally non-existent
- Changes generally require manual interaction
- Even for experienced network engineers, network changes are error-prone
- Many traditional network constructs such as VLANs, firewalls, load balancers, ACLs, and others present roadblocks to fast-paced development and DevOps-style infrastructure
- Traditional networking depends on workload placement
- Workload mobility is limited
- Firewall rule sprawl
- VLAN and IP topology sprawl
What if the network could be abstracted from the underlying physical network infrastructure and placed into the software layer? VMware NSX allows eliminating the challenges mentioned above with traditional physical networks.
What is VMware NSX?
VMware NSX is a robust software-defined networking (SDN) technology that solves complex networking challenges in the modern data center environment. It enables organizations to move rapidly to deploy new networks, change existing network designs, and effectively automate networks in code. It allows businesses to connect their virtual cloud networks and protect applications across on-premises data centers, multi-cloud environments, bare-metal workloads, and modern container infrastructure with ease. Aside from delivering software-defined networking capabilities to the enterprise, VMware NSX empowers businesses with an L2-L7 security virtualization solution. With VMware NSX, companies can manage their virtual networking and network security from a single pane of glass UI with the management and security tools in a seamless interface.
VMware NSX brings both networking and security constructs closer to where the application lives. Applications can reside inside virtual machines, bare-metal physical servers, and modern containerized applications. Regardless of where the application lives or the underlying physical network, networks can be provisioned and managed independently. Since VMware NSX is a software-defined solution and does not rely on physical networking gear, it provides logical networking and security capabilities, including:
- Logical switching – VMware NSX provides logical switching capabilities that extend Layer 2 switching boundaries across a routed Layer 3 fabric. The extensions can include both within and across data center environments and public/private clouds.
- Routing – With VMware NSX, organizations have a much more modern approach to Layer 3 routing distributed in the hypervisor kernel.
- Gateway firewall – The software-defined gateway firewall provides stateful firewall capabilities up to Layer 7, with NSX providing app identification and distributed FQDN whitelisting. Again this is distributed with centralized policy and management.
- Distributed firewall – Similar to the gateway firewall, the distributed firewall as part of the VMware NSX solution provides stateful Layer 7 firewall capabilities with app ID and distributed FQDN whitelisting
- Load balancing – Organizations can use the VMware NSX load balancer to provide L4-L7 load balancing features with SSL offloading. Other features such as server health checks and passive health checks and API interaction are part of the solution.
- Virtual Private Network (VPN) – Site-to-Site VPN, remote-access VPN, and cloud gateway services are possible with VMware NSX VPN
- NSX Gateway – You can bridge physical Layer 2 VLANs from the physical network with NSX overlay networks using the NSX Gateway
- NSX Intelligence – The NSX Intelligence platform uses automated artificial intelligence (AI) and machine learning (ML) to provide continuous monitoring and visualization for network traffic flows to recognize malicious traffic and intent
- NSX Distributed IDS/IPS – VMware NSX has evolved to provide centralized advanced threat detection and prevention engine that allows detecting and preventing east-west movement of malicious threats. It provides a distributed architecture and application context in software that can replace the functionality provided by discrete security appliances.
- Federation – For organizations managing multiple VMware NSX environments, the Federation capability allows managing and configuring numerous environments with a single pane of glass using centralized policy and enforcement
- Virtual Routing and Forwarding (VRF) – For multi-tenant environments, VMware NSX provides complete data plan isolation using the NSX Tier 0 gateway that provides separate routing tables, NAT, and edge firewall support in each VRF.
- NSX Data Center API – Developers and DevOps automation tools have access to RESTful APIs that allow interacting with VMware NSX programmatically.
- Operations – VMware NSX includes native tools such as traceflow, overlay logical SPAN, and IPFIX and also allows easy integration with other tools such as vRealize Network Insight (vRNI).
- Quality of Service (QoS) – Define software-based QoS features to applications
- Context-aware micro-segmentation – Security groups and policies with VMware NSX can automatically be created and updated based on various environmental attributes outside of the typical network constructs such as IP address, port, and others.
The logical, software-defined architecture allows easily provisioning networking non-disruptively over existing physical networks. VMware NSX logical networks can extend across data centers, public and private cloud environments, containers, and bare-metal servers.
How does VMware NSX work?
Software-defined network solutions, including VMware NSX, make use of an underlay and an overlay network. It provides the ability to separate the control and data planes between the two. Let’s see how both the underlay and overlay networks play a part in network communication with a software-defined network (SDN) solution.
- Underlay – The underlay network includes the physical network infrastructure that enables the transmission of packets. The underlay network also consists of the routing protocols needed to allow for IP connectivity between locations. Routing protocols including OSPF, IS-IS, and BGP are examples of common routing protocols for this purpose.
- Overlay – The overlay network is where the “magic” of a software-defined network happens. The overlay network is formed “on top of” the underlay physical network architecture. Both the data plane traffic and control plane signalling are controlled within the virtualized network. Multiple virtual networks can overlay on top of a single physical network. Overlay networks use overlay protocols such as VXLAN, NVGRE, OTV, and GENEVE
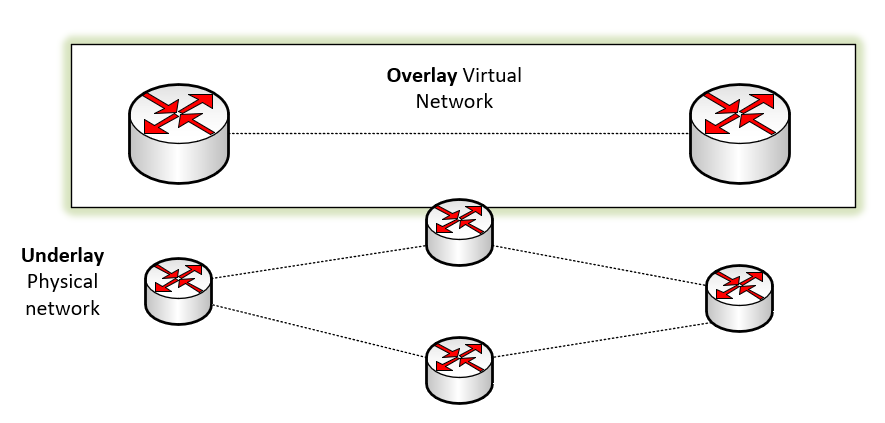
A high-level overview of the Overlay and Underlay network in software-defined networking
VMware NSX key benefits
VMware NSX provides many critical benefits to organizations looking to modernize networking operations in their environments. These include the following:
- Micro-segmentation – The notion of having a “trusted” internal network is no longer practical with new-age threats and the way attackers are compromising networks via east-west attacks
- Automated network provisioning – The ability to automate network provisioning, configuration, and security policy management allows businesses to be much more agile in their operations
- Consistent management of networking and security policies – Since logical networks can be controlled through code, it allows much more consistent management of networking and security policies
- Built-in network visualization and monitoring – VMware NSX provides monitoring and visualization of application topologies, security policies, and flow monitoring
- Advanced east-west threat prevention and distributed IPS/IDS – To bolster the built-in micro-segmentation capabilities of VMware NSX, distributed IPS/IDS provides automated threat protection and prevention capabilities. The benefits include elastic throughput, reduce false positives, improved utilization of computing capacity.
VMware NSX use cases
These are alluded to with the key benefits covered. However, what are the specific use cases for using VMware NSX solutions? These include the following:
- Security
- Multi-cloud networking
- Network automation
- Networking and security for cloud-native applications
Security
Arguably the most obvious use case with using VMware NSX is security. There is a new cybersecurity best practice model known as “Zero-Trust.” The traditional network operates on the notion of an “untrusted” zone, typically the Internet, and a “trusted” zone, which has historically included the internal LAN. With new threats that have emerged, such as ransomware and other malicious tools used by attackers, there the “trusted” network is no longer a practical approach for security
Using the Zero-Trust approach, all network traffic is viewed as untrusted, regardless of where the traffic originates. In the Zero-Trust model, even if two servers share the same network, they should not implicitly trust all network traffic communicated between them. Using micro-segmentation, distributed IPS/IDS, and context-aware firewalling, VMware NSX allows organizations to have the tools to implement a Zero-Trust model in their networks effectively. It helps to prevent attackers from compromising internal resources due to lateral east-west movement.
Multi-cloud networking
Traditional networking in a single on-premises data center can be difficult, let alone networking between data centers and even on-premises and cloud environments. With VMware NSX software-defined solutions, networking and security boundaries can be extended between heterogeneous sites. It allows stretching sites and moving workloads between on-premises and cloud environments without disruption.
Traditional physical networking cannot achieve the mobility and flexibility that VMware NSX provides for workloads. It decouples the requirements that a physical network exists in a particular location and allows networks to be placed where logically needed to solve challenging technical and business use cases.
Network Automation
One of the compelling capabilities afforded by the VMware NSX platform is the ability to automate the solution. The deployment of full-stack solutions can be accomplished in code without entering a CLI interface or deploying physical appliances. VMware NSX exposes various APIs that allow interacting with the solution through RESTful API calls. You can also integrate VMware NSX with other automation solutions such as Ansible, Terraform, and vRealize Automation, automation solutions commonly used within the enterprise.
Networking and security for cloud-native applications
VMware NSX allows your organization to provide both networking and security capabilities for modern workloads and containerized applications. You can do this with a very granular policy based on each container. It allows applying the same micro-segmentation capabilities for virtual machines to containers.
VMware NSX-V vs. VMware NSX-T
If you have been keeping up with the evolution of VMware NSX, you will be quick to note VMware NSX has evolved in the past few years from the early days of its initial releases. VMware NSX now comes in two different versions of the product. There are VMware NSX-V and VMware NSX-T. Each version of VMware NSX has specific use cases and characteristics. It is essential to recognize the differences between the two solutions and understand which version you should deploy. Let’s take a detailed comparison between VMware NSX-V and VMware NSX-T to see how the solutions are different, why NSX-T is an improvement over NSX-V, and the migration path from NSX-V to NSX-T.
What is VMware NSX-V?
VMware introduced the original VMware NSX product after VMware’s purchase in 2012 of a company called Nicira. VMware integrated Nicira’s R&D teams and shortly after that introduced the first version of VMware NSX. This became the mainstream VMware NSX-V. The “V” in the NSX-V solution stands for “vSphere.” VMware NSX-V is a vSphere-only solution. It is VMware’s software-defined networking platform supported to run in a vSphere environment. Currently, the solution is marketed as NSX Data Center for vSphere. Installing VMware NSX-V requires you have a vCenter Server in the environment. When VMware NSX-V is installed, it registers with your vCenter Server, and the solution integrates into vSphere through the connection with vCenter.
The vCenter Server is defined as the compute manager for the VMware NSX-V solution. VMware NSX-V connections are made through the vCenter Server APIs to interact with vSphere and onboard ESXi hosts. One of the reasons that VMware NSX-V is reliant on vCenter Server is the vSphere Distributed Switch (VDS) requirement for the more advanced VMware NSX-V functionality, including logical switches, etc. The vSphere Distributed Switch is a vCenter Server construct that requires a vCenter Server in the environment. Unlike the vSphere Standard Switch that resides on the ESXi host itself, vCenter Server maintains the vSphere Distributed Switch (VDS). The vCenter Server synchronizes the VDS switches with the ESXi hosts.
As described earlier with software-defined networking, an overlay network creates the virtual network on top of the underlay network or the physical network that transmits the packets. To create the overlay network, VMware NSX-V uses the VXLAN network encapsulation protocol. What is VXLAN? VXLAN is short for Virtual Extensible LAN. It is an encapsulation protocol that provides connectivity between data centers through tunneling. It effectively allows connecting two Layer 2 segments over Layer 3. VXLAN is not a VMware-only technology. It is an open standard used in many different vendor technologies, including EVPN, Cisco ACI, etc.
VXLAN uses packet encapsulation similar to VLANs that creates VXLAN tunnels between VXLAN tunnel endpoints (VTEPs). The problem with VLANs is they were developed with a fixed 12-bit field, which means there are roughly 4000 VLANs that can be provisioned in a single environment. However, VXLAN overcomes this issue as each VXLAN segment uses a 24-bit segment ID known as the VXLAN Network Identifier (VNI) for identification. The 24-bit segment ID allows up to 16 million unique VXLAN segments in the same administrative domain as opposed to the 4000 with VLANs.
Through VXLAN, VMware NSX-V can create logical, virtual networks and the ability to “stretch” and architect networks in a way that solves very complex problems. It also allows creating virtual constructs such as the L2 logical switch, distributed logical routers, load balancers, and other features.
Why is it being deprecated?
As organizations have transitioned from mainly on-premises data centers to leverage the cloud for many workloads, it became apparent a new version of VMware NSX was needed. A modern network virtualization solution needs to scale beyond VMware vSphere and allow organizations to use network virtualization with modern cloud-native platforms. For quite some time, VMware NSX-V was VMware’s preferred network virtualization solution for VMware vSphere. However, VMware introduced a new version of VMware NSX, known as VMware NSX-T (which will be described in detail to follow).
The early stages of the VMware NSX-T release lacked many of the features that enterprise customers had with VMware NSX-V and lacked the seamless installation process with VMware NSX-V. Since VMware NSX-V has been around much longer than NSX-T, there were many more third-party integrations with VMware NSX-V than NSX-T, as you would expect. In the early stages of VMware NSX-T, customers with many third-party integration requirements were better suited to install VMware NSX-V.
VMware NSX-V at this point is considered the legacy VMware NSX solution in the portfolio of VMware NSX Data Center solutions. VMware NSX-T is a much more robust and fully-featured modern implementation of VMware NSX that is no longer limited to the confines of VMware vSphere. VMware is steering customers with greenfield implementations of VMware NSX to install VMware NSX-T, even in VMware vSphere environments. They have also created a migration process with the technical tools needed to migrate from the VMware NSX-V platform to NSX-T.
VMware is committed to supporting NSX-V environments until the end of general support date. The end of general support date is January 16, 2022. The end of technical guidance given by VMware for VMware NSX-V follows on January 16, 2023.
What is VMware NSX-T?
VMware NSX-T is the new, modern release of VMware NSX Data Center. NSX-T is the solution that will be moving forward with VMware network virtualization, covering all platforms, including VMware vSphere. The “T” in NSX-T stands for “Transformers.” Intuitively, NSX-“Transformers” allows the solution to transform beyond the initial use case of network virtualization with VMware vSphere and into the realm of public cloud and modern containerized workloads.
VMware NSX-T is a very flexible solution businesses can implement with VMware vSphere and KVM hypervisors and bare-metal servers, and containerized workloads. It is the network virtualization platform VMware has chosen for their VMware on AWS cloud IaaS solution. It is also running under the hood of Amazon AWS Outposts.
VMware NSX-T is VMware’s solution to modernize networking and security in the enterprise and cloud-native environments and everything in between. You can think of VMware NSX-T as a multi-cloud solution that allows organizations to stitch networking together in an effective, efficient, and seamless way. This type of solution is needed as modern applications may contain many different infrastructure components. It may include virtual machines, containers, and even bare-metal workloads.
Businesses need an API-driven solution, flexible, intrinsic security, and streamlined operations to solve the challenges with the diverse infrastructure and cloud environments that back modern applications. These are the types of challenges that VMware NSX-T is purpose-built to address.
VMware NSX-T removes the requirement for VMware vCenter Server to deploy the solution. You can deploy VMware NSX-T VMware ESXi host transport nodes without vCenter Server altogether.
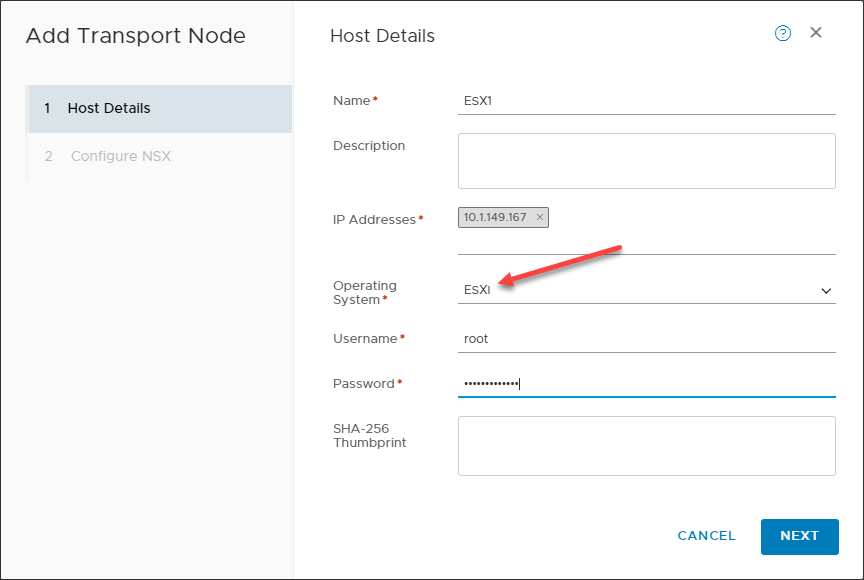
Adding a VMware NSX-T ESXi transport node
Compatibility and interoperability with VMware vSphere is still very strong. VMware vCenter Server is now referred to as a Compute Manager. You add vCenter as a Compute Manager to allow easy integration with ESXi hosts if you want to onboard ESXi hosts in mass.
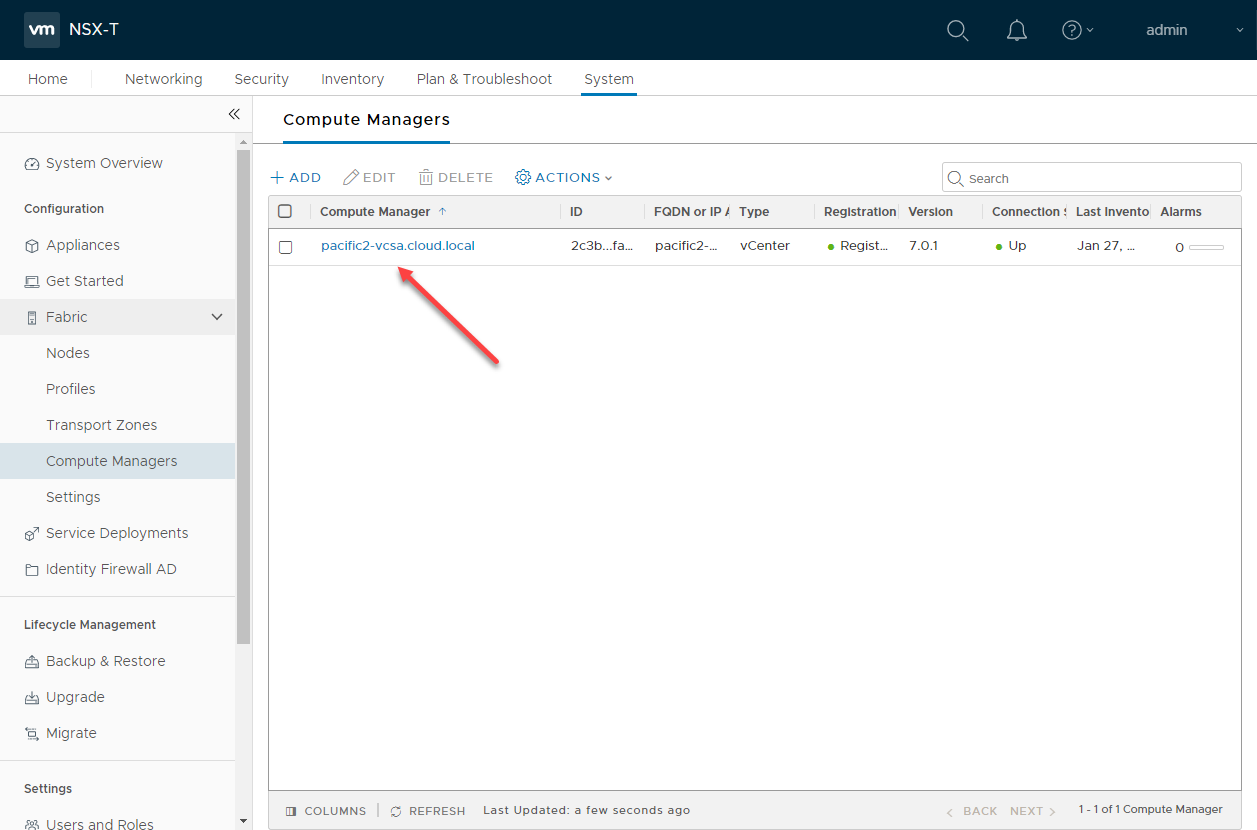
Adding vCenter Server as a Compute Manager in NSX-T
It is due to VMware NSX-T being a standalone solution in its own right. It does not depend on a particular hypervisor compute manager such as VMware vCenter Server to function. However, many of the basic concepts highlighted with VMware NSX-V apply with NSX-T. VMware NSX-T uses an encapsulation protocol to create an overlay network on top of the physical network underlay.
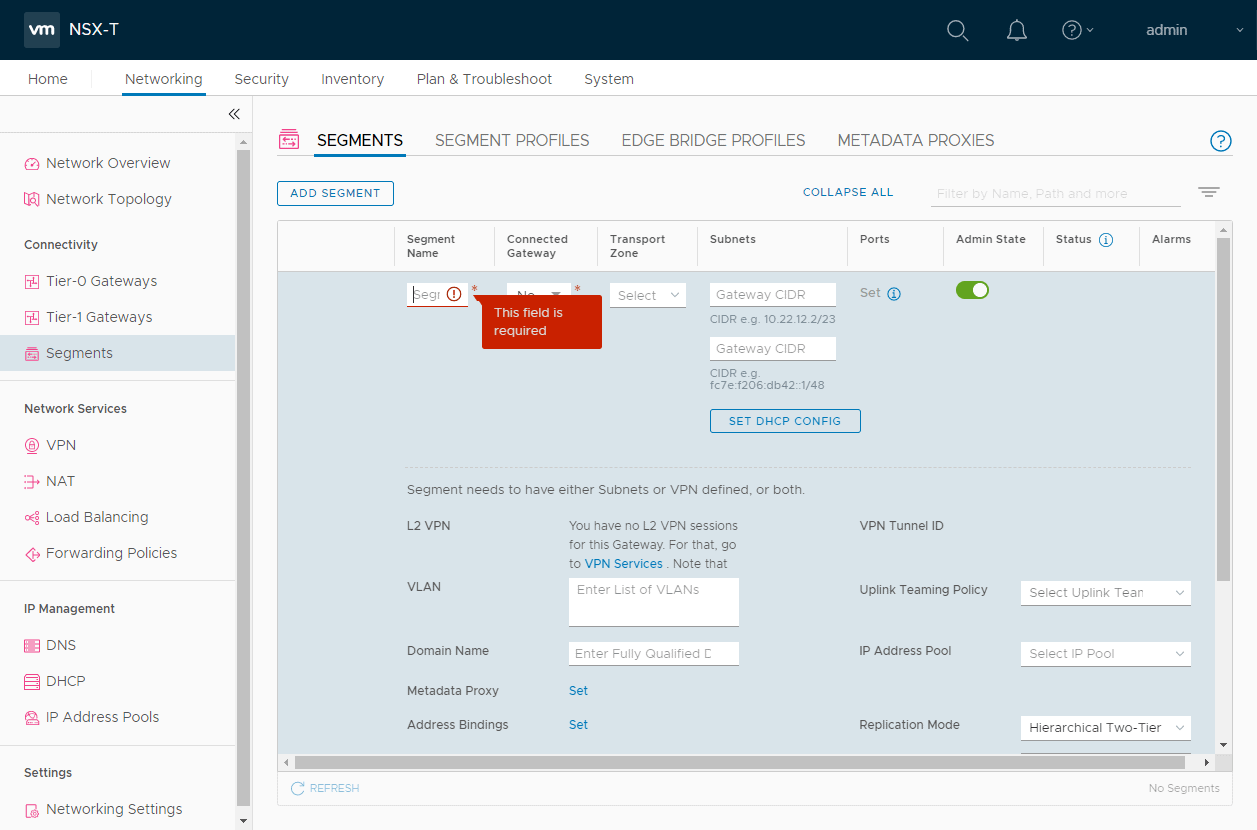
Adding virtual network segments in NSX-T
Instead of using the very common VXLAN, VMware NSX-T has moved forward using the GENEVE network encapsulation protocol. What is GENEVE? GENEVE is short for Generic Network Virtualization Encapsulation. Compared to other popular network encapsulation protocols, GENEVE is believed to be the modern technology moving forward. It helps to solve many of the problems or limitations found with earlier encapsulation protocols like VXLAN. While it works almost identically to VXLAN, it offers more flexibility in its implementation because of control plane independence.
GENEVE is an open standard that does not include information or specification for the control plane. The IETF draft states this:
Although some protocols for network virtualization have included a control plane as part of the tunnel format specification (most notably, the original VXLAN spec prescribed a multicast learning-based control plane), these specifications have largely been treated as describing only the data format. The VXLAN frame format has actually seen a wide variety of control planes built on top of it.
There is a clear advantage in settling on a data format: most of the protocols are only superficially different, and there is little advantage in duplicating effort. However, the same cannot be said of control planes, which are diverse in very fundamental ways. The case for standardization is also less clear given the wide variety in requirements, goals, and deployment scenarios.
Another slight variation, when compared to VXLAN, is the terminology difference between the tunnel endpoints. While VXLAN tunnel endpoints are referred to as VTEPs, the GENEVE tunnel endpoints are simply called tunnel endpoints (TEPs). With GENEVE under the hood of VMware NSX-T, NSX-T has “future-proofing” built into the solution from an encapsulation protocol perspective.
While VMware NSX-V uses a more traditional approach to routing, VMware NSX-T introduces a new two-tier routing architecture that is better suited for multi-tenant environments and scaling for today’s very complex cloud architectures. With VMware NSX-T, it has introduced a new TIER-0 and TIER-1 routing topology.
Why should organizations migrate to VMware NSX-T?
If you are running VMware NSX-V, besides the end of life looming in 2022, why should organizations migrate to VMware NSX-T from a feature perspective? VMware NSX-T provides an extremely robust solution with modern features and capabilities that align with the cloud-native applications organizations are using today. VMware cites four reasons that organizations should migrate from NSX-V to NSX-T from a feature perspective. These include:
- Scale-out networking, including NSX Federation – VMware NSX-T provides the means to federate and manage numerous installations of VMware NSX across multiple locations.
- Full-stack networking for modern distributed applications – This sets VMware NSX-T apart from VMware NSX-V. NSX-T is purpose-built to handle modern applications, including containerized workloads, something NSX-V was never designed to do.
- NSX Intelligence with best-in-class security – NSX Intelligence is a modern AI and ML-driven solution that provides proactive security intelligence in your environment to find and prevent cybersecurity attacks.
- Networking and security automation – NSX-T provides a robust API-driven interface that helps to simplify network automation.
- More intuitive dashboard and monitoring capabilities
New features in VMware NSX-T 3.1
VMware NSX-T 3.1 contains many new features, including the following:
- Cloud scalability improvements
- Simplified operations
- East-west traffic security improvements
- Distributed IDS/IPS
- NSX Intelligence 1.2
- NSX-V to NSX-T Migration for large scale networks
Cloud scalability improvements
VMware NSX-T 3.1 contains many new cloud scalability improvements. These include NSX T auto-scaling build into the platform that allows growing as your network needs change. NSX-T 3.1 provides clustering support for the NSX Global Manager, simplified disaster recovery workflows, a terraform provider for better automation, and improved scalability for large deployments.
New enhancements to multicast traffic have also been provided. It enables multicast in a multi-tenant environment. New tenant multicast deployments can be automated with APIs and no longer require changing the network’s underlying configuration.
Simplified operations
VMware NSX-T 3.1 provides simplified operations for use with both private and public cloud environments. It includes deep integration with vREalize Network Insight (vRNI) to enhance network modelling, configuration, and intent verification. It helps to understand the impacts of network changes as well as offers better network planning overall.
With the new vSphere 7.0 and higher releases, VMware has introduced the new vSphere Lifecycle Manager (vLCM). With vLCM, organizations can access simplified lifecycle management across their environment that understands VMware NSX-T and provides NSX lifecycle management.
VMware NSX-T provides a better dashboard for monitoring and viewing traffic, compliance, and other reporting. It allows admins to get information about the network quickly.
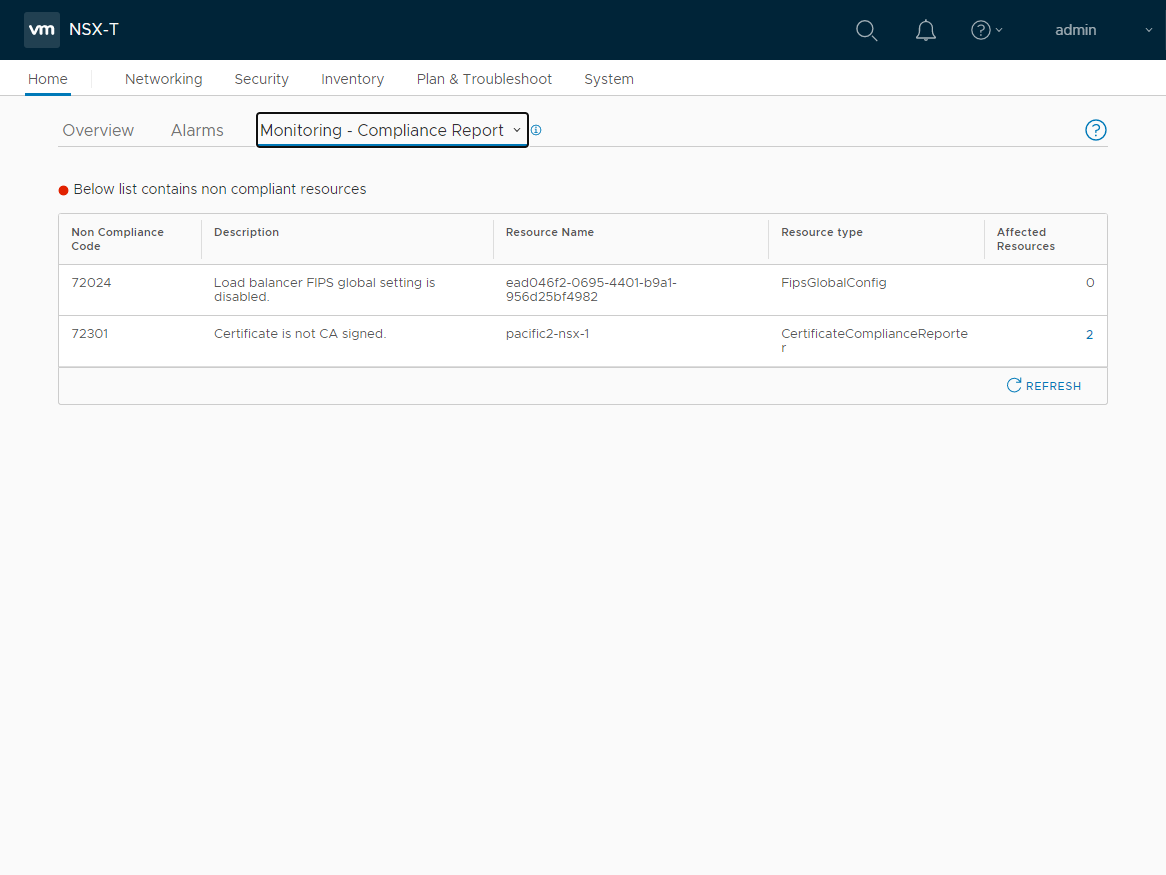
VMware NSX-T monitoring and compliance report
The VMware NSX-T dashboard is searchable and displays information about the virtual network environment and security in a single intuitive dashboard.
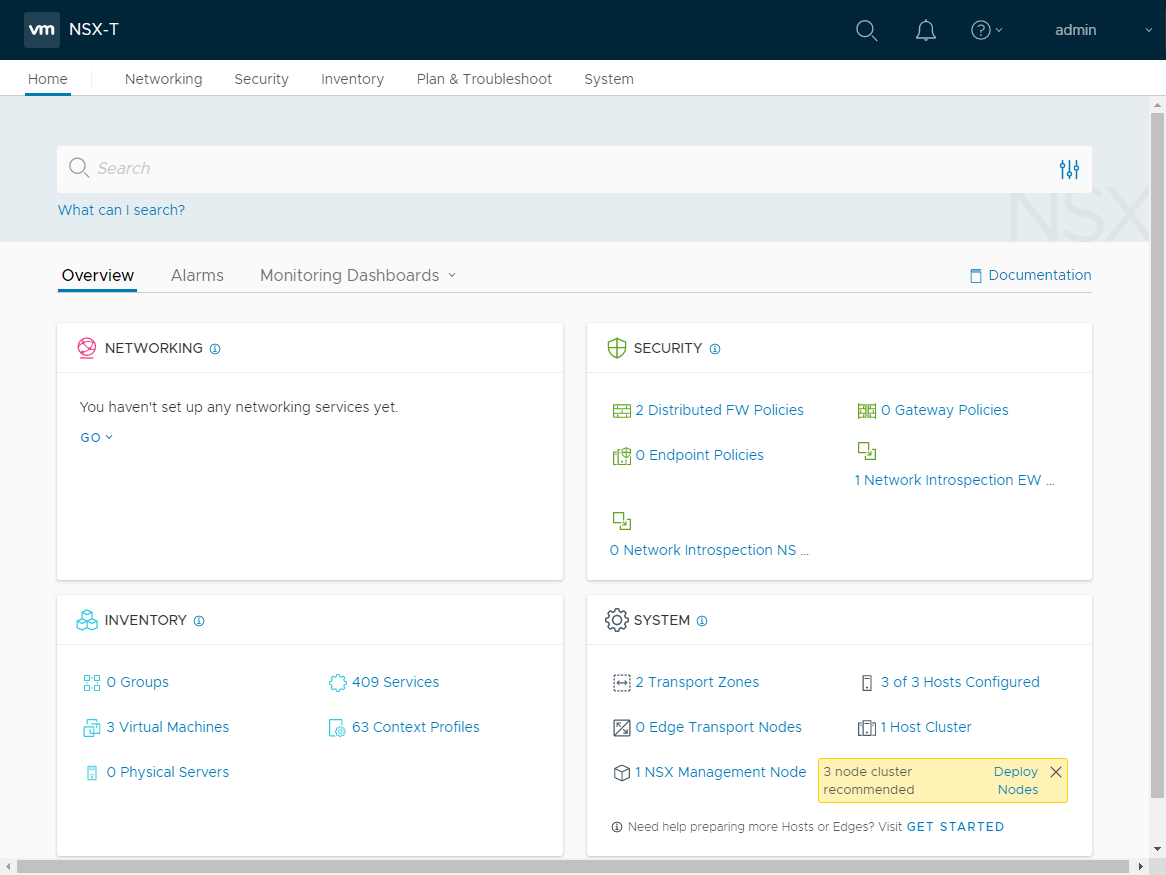
VMware NSX-T provides an intuitive seamless dashboard for viewing the environment
East-west traffic security improvements
VMware has introduced the ability to purchase Internal Firewall and Advanced Threat Prevention (ATP) independently of the networking features in VMware NSX-T 3.1. The Advanced Threat Prevention capabilities include Distributed IDS/IPS, Network Traffic Analytics/Networking Detection and Response, and Network Sandboxing.
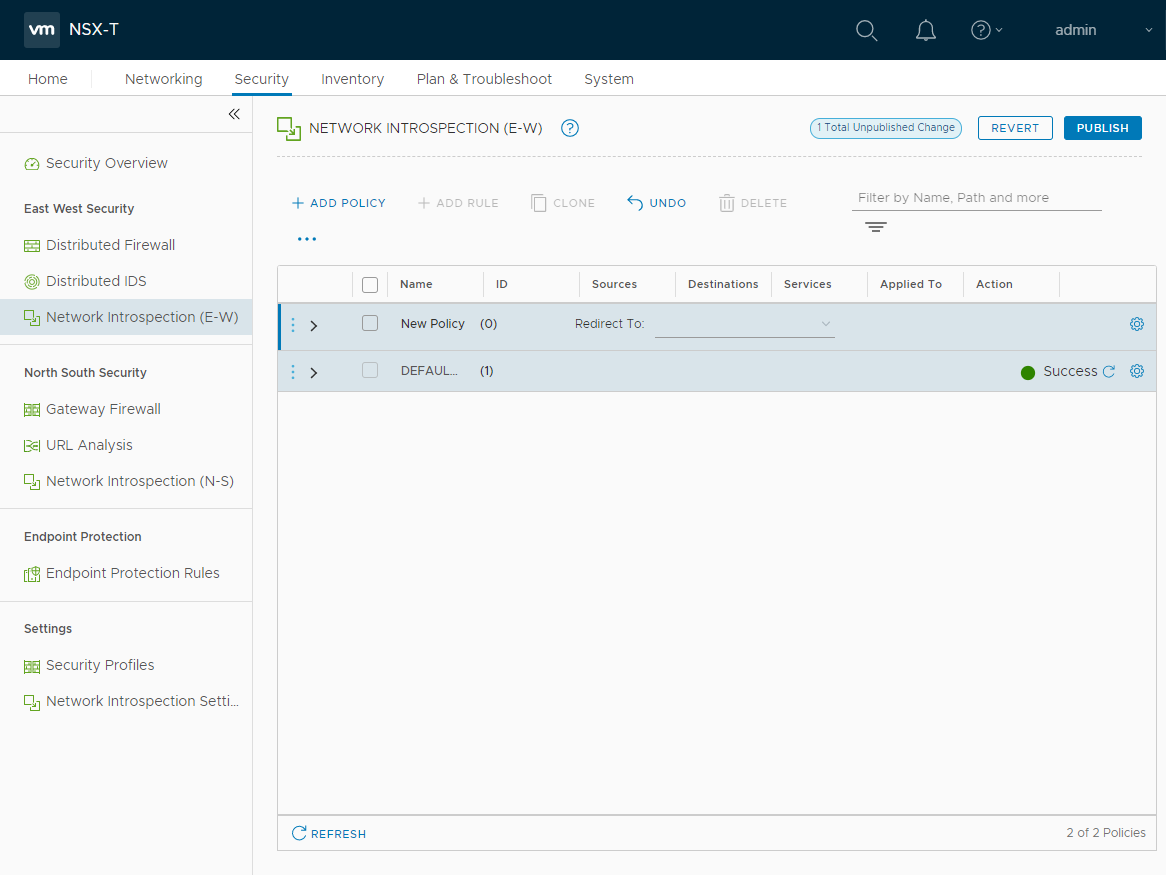
VMware NSX-T provides network introspection capabilities for east-west traffic
Distributed IDS/IPS
VMware NSX-T 3.1 introduces the world’s first distributed IDS/IPS solution that provides the ability to detect and stop east-west lateral threat movement across your environment. It also helps to replace discrete hardware appliances and strengthens compliance capabilities.
The IDS/IPS’s virtual patching capabilities help patch vulnerabilities at a workload level without new signatures from an endpoint security perspective. From a performance perspective, the overhead is minimal.
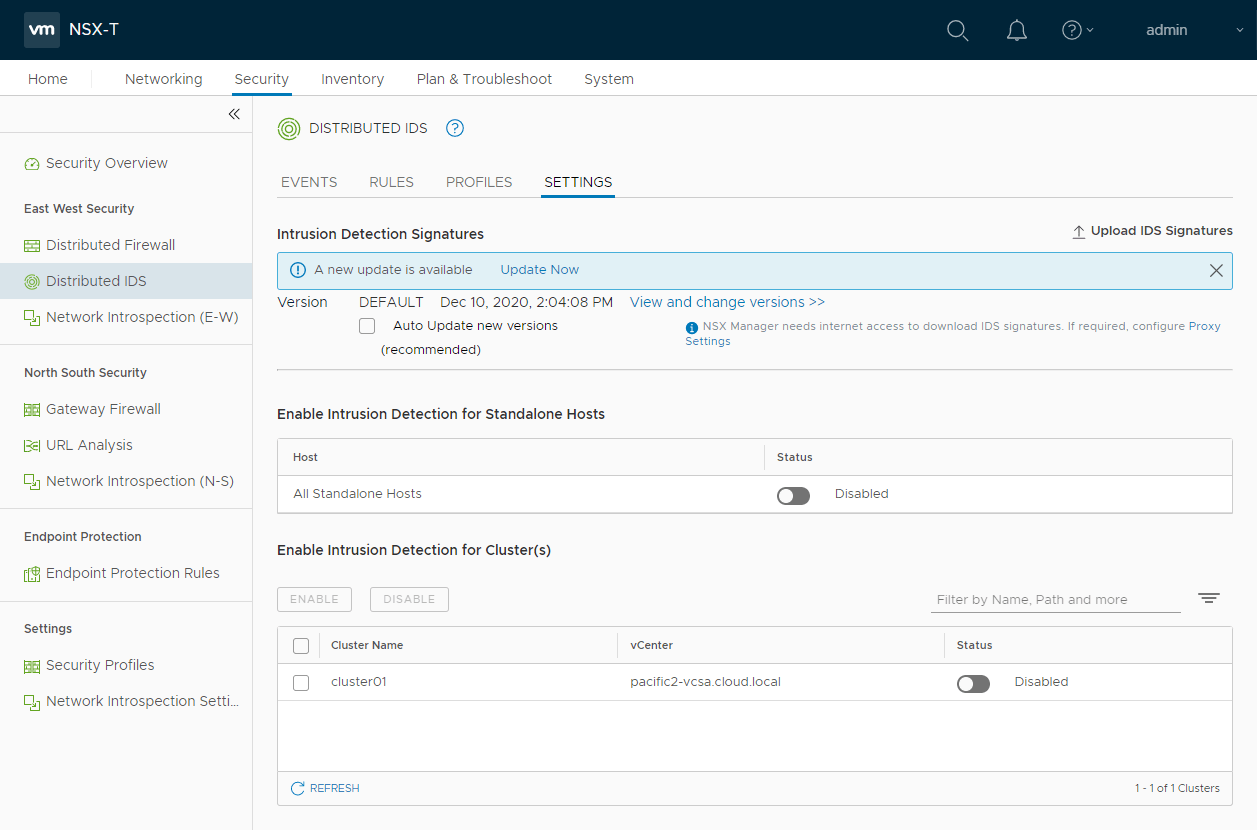
VMware NSX-T Distributed IDS/IPS
NSX Intelligence 1.2
With NSX Intelligence 1.2, VMware has added NSX Intelligence’s ability to cover physical servers and improves recommendations across the entire environment, including VMs and bare-metal servers. This also includes L7 content profile recommendations with App-ID support. Visualizations include the display of user and process level context from workloads.
VMware NSX-T NSX Intelligence provides a modern security solution
VMware NSX-T application context
NSX-V to NSX-T Migration for large scale networks
VMware has added integration with vRealize Automation and provided Migration Coordinator enhancements. It is all to help organizations accelerate their migrations from NSX-V to NSX-T. The migration coordinator’s new capabilities allow customers to migrate things like firewall rules with lift and shift ease from NSX-V environments over to NSX-T.
NSX-T migration coordinator
Comparing NSX-V with NSX-T
Any way you look at it, VMware NSX is a revolutionary technology. It has evolved into an even more powerful solution since its inception in the early days of 2012. Let’s review by comparing the differences between the two solutions.
Reliance on VMware vCenter
VMware NSX-V is a VMware vSphere-only solution. It is VMware’s initial NSX solution based on the original code acquired from Nicira. With VMware NSX-V, it requires a connection to vCenter Server for integration with the ESXi hosts. Another reason for the vCenter Server integration is the requirement for vSphere Distributed Switches (VDS). The VDS is required for the advanced functionality that VMware NSX-V provides such as Logical Switching.
VMware NSX-T does not require a vCenter Server and allows interacting with ESXi hosts directly and onboard those as transport nodes. VMware vCenter Server can be used as a compute manager to integrate with multiple ESXi hosts. However, the key here is that VMware NSX-T is not a vSphere-specific network virtualization platform.
Overlay technology
VMware NSX-V uses Virtual Extensible LAN (VXLAN) as the overlay technology that creates the virtualized network infrastructure. VXLAN is a vendor-neutral protocol and provides a 24-bit segment ID that provides 16 million possible virtual network segments. It is far above the traditional VLAN, which provides roughly 4000 useable network segments.
VMware NSX-T uses the Generic Network Virtualization Encapsulation (GENEVE) as the overlay network encapsulation protocol. GENEVE is regarded as an even more modern encapsulation protocol that helps overcome some of the limitations of more traditional network encapsulation protocols like VXLAN.
Routing
VMware NSX-V uses a more traditional routing architecture. VMware NSX-T introduces a multi-tier routing architecture using what is known as a TIER-0 and TIER-1 routing topology. It is a much better approach for today’s multi-tenant environments.
Multi-cloud capabilities
In terms of multi-cloud capabilities, VMware NSX-V is limited. Since it is limited to VMware vSphere environments, it is not considered a multi-cloud platform. Even “VMware” cloud environments such as VMware Cloud on AWS do not use VMware NSX-V, but rather VMware NSX-T.
VMware NSX-T is a multi-cloud network virtualization technology. Since it is not a VMware vSphere-only technology and is designed for modern workloads, VMware NSX-T is a true multi-cloud platform. It allows organizations to leverage the power of virtual networking on-premises as well as in the cloud.
Feature parity
In the early days of the solution, VMware NSX-T did not have feature parity with VMware NSX-V. However, now, VMware NSX-T has effectively surpassed VMware NSX-V in terms of what it can do and the powerful integrations with other solutions like NSX Intelligence.
Lifecycle and End of Life
VMware NSX-V is a solution that will be going end of life in 2022 and then extended technical guidance will be ended in 2023. Considering this fact alone, VMware NSX-T is a solution that organizations will be installing moving forward for greenfield installations. Also, environments that are currently on VMware NSX-V will need to migrate to VMware NSX-T.
VMware NSX-T is the modern solution moving forward for both VMware vSphere and multi-cloud environments. New features and functionality will be included in VMware NSX-T. At this point, VMware NSX-V will be maintained and patched. It would not be surprising to see a few new features added. However, for the most part, VMware NSX-T will receive the majority of new capabilities.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









