Save to My DOJO
Table of contents
Historically and like most malware, ransomware has been targeting Windows operating systems primarily. However, cases of Linux and MacOS being infected are being seen as well. Attackers are being more proficient and keep evolving in their attacks by targeting critical infrastructure components leading to ransomware attacks on VMware ESXi. In this article, you’ll learn how Ransomware targets VMware infrastructure and what you can do to protect yourself.
What is Ransomware?
Ransomware are malicious programs that work by taking the user’s data hostage in exchange for a hefty ransom.
There are essentially 2 types of Ransomware (arguably 3):
-
- Crypto Ransomware: Encrypts files so that the user cannot access them. This is the one we are dealing with in this blog.
-
- Locker Ransomware: Lock the user out of his computer by encrypting system files.
-
- Scareware: Arguably a third type of ransomware that is actually a fake as it only locks the screen by displaying the ransom page. Scanning the system with an Antivirus LiveCD will get rid of it quite easily.
A user computer on the corporate network is usually infected through infected USB drives or social engineering techniques such as phishing emails and shady websites. Another occurrence includes attacking a remote access server publicly exposed through brute-force attacks.
The malware then uses a public key to encrypt the victim’s data, which can span to mapped network drives as well. After which the victim is asked to make a payment to the attacker using bitcoin or some other cryptocurrency in exchange for the private key to unlock the data, hence the term Ransomware. If the victim doesn’t pay in time, the data will be lost forever.
As you can imagine, authorities advise against paying the ransom as there is no guaranty the bad actor will deliver on his end of the deal so you may end up paying the big bucks and not recover your data at all.
Can Ransomware affect VMware?
While infecting a Windows computer may yield a reward if the attacker gets lucky, chances are the OS will simply be reinstalled, no ransom is paid and the company will start tightening security measures. Game over for the bad guys.
Rather than burning bridges by locking a user’s workstation, they now try to make a lateral move from the infected workstation and target critical infrastructure components such as VMware ESXi. That way they hit a whole group of servers at once.
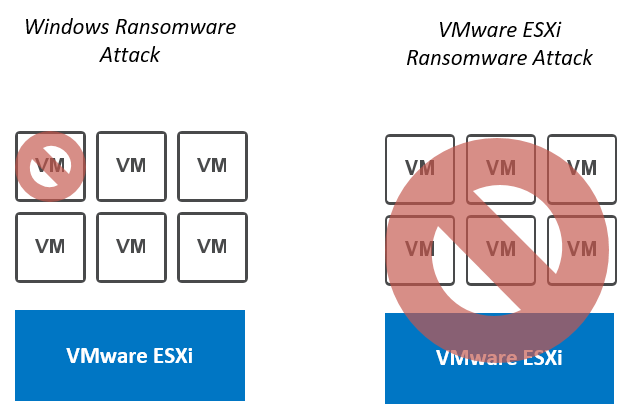
“VMware ESXi ransomware impact all the VMs running on the hypervisor”
From the standpoint of an attacker, infesting a vSphere host, or any hypervisor for that matter, is an “N birds, 1 stone” type of gig. Instead of impacting one workstation or one server, all the virtual machines running on the host become unavailable. Such an attack will wreak havoc in any enterprise environment!
How does a Ransomware Attack Work?
In the case of targeted attacks, the bad actor works to gain remote access to a box in the local network (LAN), usually a user computer, and then make a lateral move to access the management subnet and hit critical infrastructure components such as VMware ESXi.
There are several ways a ransomware attack on VMware ESXi can happen but reports have described the following process.

“The ransomware attack on VMware ESXi described in this blog is broken down into 5 stages”
Stage 1: Access local network
Gaining access to the LAN usually goes either of 2 ways:
-
- A malware is downloaded in a phishing email or from a website. It can also come from an infected USB stick.
-
- The attacker performs a Brute force attack against a remote access server exposed to the internet. This seems more unusual as it involves more resources and knowledge of the target. Brute force attacks are also often caught by DDoS protection mechanisms.

“Ransomware spread through malicious email attachments, websites, USB sticks”
Stage 2: Escalate privileges
Once the attacker has remote access to a machine on the local network, be it a workstation or a remote desktop server, he will try to escalate privileges to open doors for himself.
Several reports mentioned attackers leveraging CVE-2020-1472 which is a vulnerability in how the Netlogon secure channel connections are done. The attacker would use the Netlogon Remote Protocol (MS-NRPC) to connect to a domain controller and gain domain administrator access.
Stage 3: Access management network
Once the bad actors have domain administrator privileges, they can already deal a large amount of damage to the company. In the case of a ransomware attack on VMware ESXi, they will use it to gain access to machines on the management network, in which the vCenter servers and vSphere ESXi servers live.
Note that they might even skip this step if the company made the mistake to give user workstations access to the management network.
Stage 4: VMware ESXi vulnerabilities
When the attackers are in the management network, you can only hope that all the components in your infrastructure have the latest security patches installed and strong password policies. At this point, they are the last line of defense, unless a zero-day vulnerability is being leveraged in which case there isn’t much you can do about it.
Several remote code execution vulnerabilities have been exploited over the last year or so against VMware ESXi servers and vCenter servers.
The two critical vulnerabilities that give attackers access to vSphere hosts relate to the Service Location Protocol (SLP) used by vSphere to discover devices on the same network. By sending malicious SLP commands, the attacker can execute remote code on the host.
-
- CVE-2019-5544: Heap overwrite issue in the OpenSLP protocol in VMware ESXi.
-
- CVE-2020-3992: Use-after-free issue in the OpenSLP protocol in VMware ESXi.
-
- CVE-2021-21985: Although no attack mentions it, we can assume the vCenter Plug-in vulnerability discovered in early 2021 can be a vector of attack as well. Accessing vSphere hosts is fairly easy once the vCenter is compromised.
They can then enable SSH to obtain interactive access and sometimes even change the root password or SSH keys of the hosts.
Note that the attacker may not even need to go through all that trouble if he manages to somehow recover valid vCenter of vSphere credentials. For instance, if they are stored in the web browser or retrieved from the memory of the infected workstation.
Stage 5: Encrypt datastore and request ransom
Now that the attacker has access to the VMware ESXi server, he will go through the following steps to lock your environment for good.
-
- Uninstall Fault Domain Manager or fdm (HA agent) used to reboot VMs in case of failure.
-
- Shut down all the virtual machines.
-
- Encrypt all virtual machine files using an ELF executable, derived from an encrypting script that targets Linux machines. This file is usually named svc-new and stored in /tmp.
-
- Write a ransom file to the datastore for the administrator to find.
Note that there are variations of the ransomware attack on VMware ESXi, which themselves are ever-evolving. Meaning the steps described above represent one way things can happen but your mileage may very well vary.
How to protect yourself from ransomware attacks on VMware ESXi
If you look online for testimonies, you will find that the breach never comes from a hooded IT mastermind in an ill-lit room that goes through your firewalls by frantically typing on his keyboard like in the movies.
The reality is nowhere near as exciting. 9 times out of 10, it will be an infected attachment in a phishing email or a file downloaded on a shady website. This is most often the doing of a distracted user that didn’t check the link and executed the payload without thinking twice.
Ensure at least the following general guidelines are being enforced in your environment to establish a first solid line of defense:
VMware environment-related recommendations
-
- If you need to open internet access on your vCenter, enforce strong edge firewall rules and proxy access to specific domains. Do not expose vCenter on the internet!!! (Yes, it’s been done).
-
- Enforce the vSphere Security Configuration Guide (previously Hardening guide).
-
- Avoid installing third party vCenter plugins.
-
- Enable Secure Boot and vSphere Trust Authority on vSphere hosts.
-
- Don’t join your vSphere hosts to Active Directory.
-
- Set VMware ESXi shell and SSH to manual start and stop.
-
- Don’t use the same password on all the hosts and out-of-band cards.
Some recommend not to add Active Directory as an Identity Source in vCenter Server. While this certainly removes a vector of attack, configuring Multi-Factor Authentication also mitigates this risk.
Industry standards
-
- Educate your users and administrators through educational campaigns.
-
- Ensure the latest security patches are installed as soon as possible on all infrastructure components as well as backups servers, workstations…
-
- Segregate the management subnets from other subnets.
-
- Connect to the management network through a jump server. It is critical that the jump server must:
-
-
- Be secured and up to date
-
-
-
- Accessible only through Multifactor authentication (MFA)
-
-
-
- Must only allow a specific IP range.
-
-
- Restrict network access to critical resources only to trained administrators.
-
-
- Ensure AD is secured and users/admins are educated on phishing attacks.
-
-
-
- Apply least privilege policy.
-
-
-
- Use dedicated and named accounts.
-
-
-
- Enforce strong password policies.
-
-
-
- Segregate Admin and Domain admin accounts on AD.
-
-
-
- Log out users on inactivity on Remote Desktop Servers.
-
-
- Don’t save your infrastructure password in the browser.
-
- Use Multi-Factor Authentication (MFA) where possible, at least on admin accounts.
-
- Forward infrastructure logs to a Syslog server for trail auditing.
-
- Ensure all the workstations and servers have a solid antivirus with regularly updated definitions.
Where do backups fit in all this?
While there are decryption tools out there, they will not always work. In fact, they almost never will.
Restoring from backup is essentially the only way known to date that you can use to recover from a ransomware attack on VMware ESXi. You can use Altaro VM Backup to ensure your environment is protected.
Because attackers know this well, they will try to take down the backup infrastructure and erase all the files so your only option left is to pay the ransom. Which, as mentioned previously, is no guaranty that you get your files back.
Because of it, it is paramount to ensure your backup infrastructure is protected and secure by following best practices:
-
- Avoid Active Directory Domain integration or use multi-factor authentication (MFA).
-
- Do not use the same credentials for access to the VMware and Backup infrastructures.
-
- Follow the 3-2-1 backup strategy at the very least.
-
- Test your backups regularly.
-
- Keep the backup infrastructure on a dedicated network. Also called Network Air-Gap.
-
- Sufficient backup retention to avoid backing up infected data.
-
- Maintain offsite read-only backups (air gap).
You can also check our dedicated blog for more best practice recommendations: Ransomware: Best Practices for Protecting Backups.
NIST controls for data integrity (National Institute of Standards and Technology)
VMware documents solutions for combatting ransomware by incorporating the National Institute of Standards and Technology (NIST) controls specific to data integrity. You can find VMware’s recommendations and implementation of the NIST in this dedicated document:

“National Institute of Standards and Technology logo”
The NIST framework is broken down into 5 functions:
-
- Identify and Protect: SP 1800-25
-
- Detect and Respond: SP 1800-26
-
- Recover: SP 1800-11
In the VMware document linked above, you will find Detect, Protect and Respond recommendations that apply to various environments such as private cloud, hybrid cloud or end-user endpoints.
So How Worried Should I be?
Ransomware have always been one of the scary malware as they can deal a great amount of damage to a company, up to the point of causing some of them to go into bankruptcy. However, let us not get overwhelmed by these thoughts as you are not powerless against them. It is always best to act than to react.
In fact, there is no reason for your organization to get hit by a ransomware as long as you follow all the security best practices and you don’t cut corners. It might be tempting at some point to add an ALLOW ALL/ALL firewall rule to test something, give a user or service account full admin rights, patch a server into an extra VLAN or whatever action you know for a fact would increase your security officer’s blood pressure. In such a case, even if there is a 99.9% chance things are fine, think of the consequences it could have on the company as a whole should you hit that 0.1% lurking in the back.
If you are reading this and you have any doubts regarding the security of your infrastructure, run a full audit of what is currently in place and draw a plan to bring it into compliance with the current industry best practices as soon as possible. In any case, patch your systems as soon as possible, especially if you are behind!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









