Save to My DOJO
Table of contents
What’s New in 6.5: Security
vSphere 6.5 released a lot of new features! They’ve spent a lot of time focusing on security in this release with some enhancements in security. I wanted to cover some of these new features in this post.
Virtual Machine Encryption
Unlike traditional encryption, Virtual Machine Encryption happens at hypervisor layer and not in Guest OS. It does not rely on the guest operating system type as well. You can use any OS and know 100%, that the machine has been encrypted. As I/O comes out of the virtual disk controller in the VM, it is immediately encrypted by a module in the kernel before being send to the kernel storage layer. When setting it up, you apply the encryption policy to the virtual machine using the virtual machine storage policy. Once encryption policies are applied, the VM, vmdk and VM home files will get encrypted. Guest operating systems do not have access to the keys! So you won’t end up with a user trying to mess with it. How cool is that?
In vSphere 6.5, vCenter is a KMIP client and works with several different KMIP 1.1 key managers. So you have a lot of flexibility there when you’re setting it up. The keys are not stored in vCenter. As long as the VM is running on an ESXi host, the keys are stored in the ESXi host memory.
When an encryption enabled virtual machine gets powered on, vCenter server as a KMIP client retrieves the key from the key manager and sends that to the VM encryption module in the ESXi hypervisor and unlocks the key.
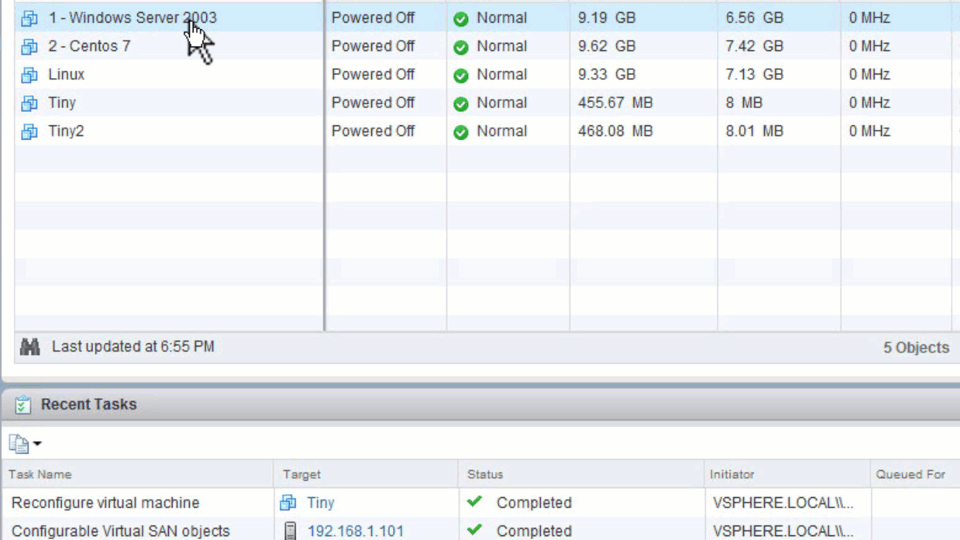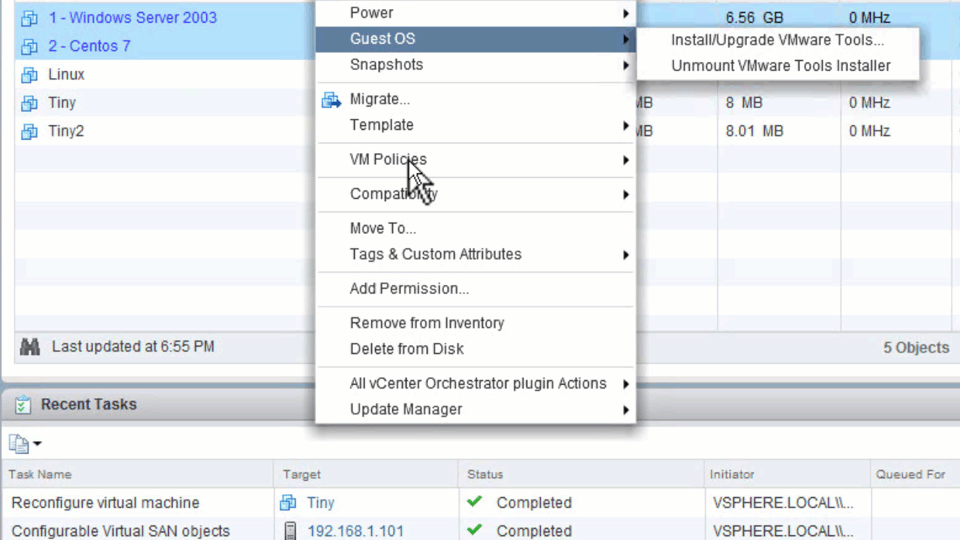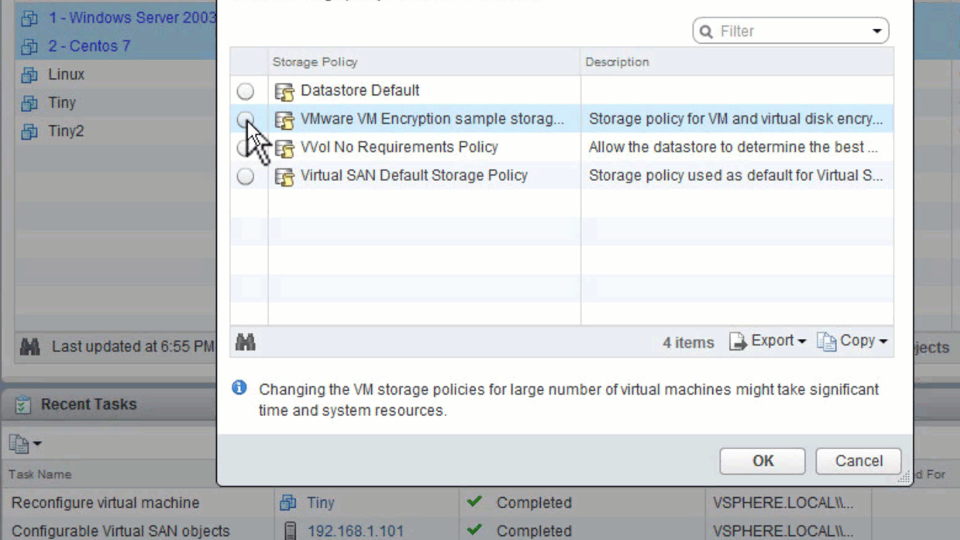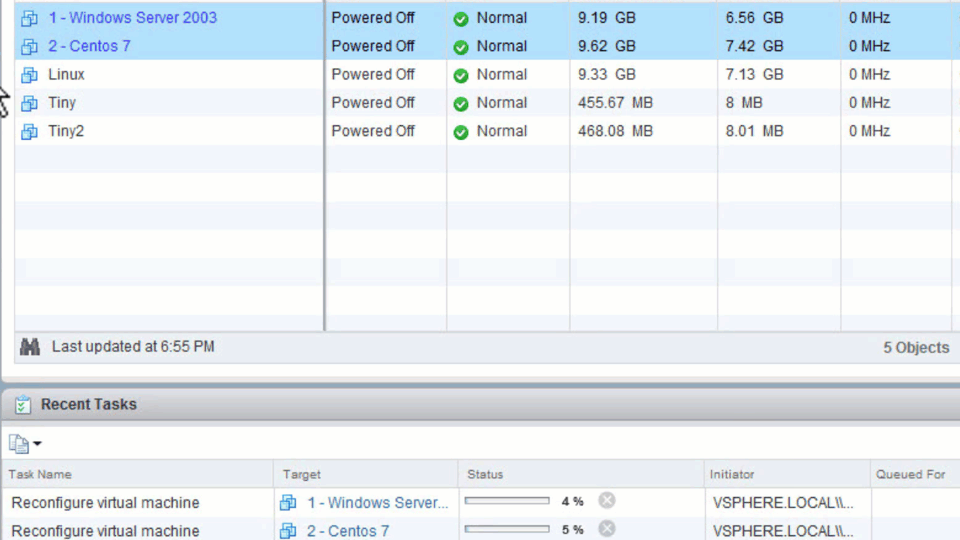
Image Source: VMware
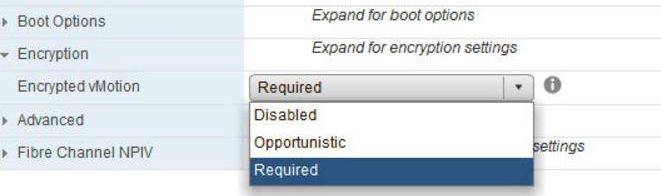
vMotion Encryption
Another cool new feature is vMotion encryption. It is exactly what it sounds like. You’re basically encypting the vMotion operation of the virtual machine from one host to another. A common misconception is that you’re encrypting the vmkernel network used for vMotion. That’s not the case here. Instead, designated VMs get a randomly generated certificate from vCenter, which is packaged up and forwarded to the participating vMotioning hosts for the VM’s transfer, protecting the data-in-motion.
ESXi and VM Secure Boot
UEFI secure boot has been around for awhile, but now with vSphere 6.5 we can now enable it within a datacenter, both for the host and the virtual machines themselves. If it’s enabled, you can’t install unsigned code whatsover. ESXi will only boot and use signed code. The UEFI firmware validates the signature of the ESXi kernel against a digital certificate in the UEFI firmware, making sure that only a properly signed kernel boots. For ESXi, VMware has taken Secure Boot a step further by adding cryptographic assurance of all components of ESXi. (This includes other VIBs you might be using!)
I’m looking forward to what’s next!
[the_ad id=”4738″][the_ad id=”4796″]


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!








