Save to My DOJO
Last year we were all dealing from the ramifications of patching the Spectre Meltdown vulnerability. It was many hours of countless “patching maintenance” windows to get all devices in a secure state. This year is the year of Zombieload – a new speculative execution variant that Intel recently reported. The new vulnerability exists so far only on Intel chips leaving AMD and ARM unaffected and can affect chips as old as 2011. The vulnerability was apparently discovered by security researchers and can be used to perform various attacks such as extracting AES keys, accessing data from another VM used by the active or sibling logical CPU. It can even be used to access data from another user session in applications.
A video was recently uploaded to youtube demonstrating how Zombieload can be used to obtain web browsing data from another VM that’s using Tor the anonymous web browser:
Zombieload Vulnerability Patches
Security researchers have revealed a white paper on Zombieload describing the vulnerability in great detail. In their conclusion for remediation, they state that “disabling hyperthreading is the only possible workaround to mitigate Zombieload on current processors.” So expect many of the vulnerability patches to contain various changes to microcode and disable hyper threading.
Intel also reported that their patches will have a minimial performance impact. Still, as IT Pros, these patches MUST be tested before rolling out. Last year there were reported issues with the Meltdown/Spectre patches and Zombieland will most likely go through the same.
Below are some of the patches that the major vendors have released
VMware Patch – Updates have been released for the following VMware products affected:
- VMware vCenter Server (VC)
- VMware vSphere ESXi (ESXi)
- VMware Workstation Pro / Player (WS)
- VMware Fusion Pro / Fusion (Fusion)
- vCloud Usage Meter (UM)
- Identity Manager (vIDM)
- vCenter Server (vCSA)
- vSphere Data Protection (VDP)
- vSphere Integrated Containers (VIC)
- vRealize Automation (vRA)
MacOS Patch – Already deployed fix to the latest Mojave and Safari browser updates.
Microsoft Patch – Recommended action is to install OS updates and possibly disable Hyper-threading in order to be completely protected.
HP Workstations Patch – HP is in the process of releasing fixes for each product that is affected by the vulnerability.
Google Patch – Each Google product has its own recommendation:
- Google Infrastructure that runs google products like Youtube, Search, Maps – No customer action needed
- Android – Only Intel-based Chrome OS devices are affected, updates are handled by Chrome OS
- Google Apps/G Suite – No customer action needed
- Google Chrome Browser – Follow OS vendor instructions and keep Chrome up to date
- Chrome OS – No customer action needed
- Google Search Appliance – No customer action needed
- Google Wifi/OnHub – No customer action needed
Citrix Patch – Recommends that all Citrix Virtual Apps and Desktops customers update their OS and hardware. For Citrix hypervisors, there is an update here.
Dell Patch – EMC servers have a BIOS update that addresses the vulnerability.
Linux Distributions
Public Cloud Service Providers
Amazon AWS Patch – “AWS has designed and implemented its infrastructure with protections against these types of bugs, and has also deployed additional protections for MDS. All EC2 host infrastructure has been updated with these new protections, and no customer action is required at the infrastructure level. ”
Azure Patch – “Microsoft has deployed mitigations across all our cloud services. The infrastructure that runs Azure and isolates customer workloads from each other is protected. This means that a potential attacker using the same infrastructure can’t attack your application using these vulnerabilities.”
Google Cloud Patch – “The infrastructure that runs Google Cloud and isolates customer workloads from each other is protected against known attacks. But for some Google Cloud products, clients will need to patch their runtime environments.”
Microsoft PowerShell Speculation Control Module
One of the most popular PowerShell modules that exist on the PowerShell gallery is called Speculation Control.
To install the module run the following command on an administrative PowerShell console to install the module from the PowerShell Gallery:
Install-Module -Name SpeculationControl
After the module is installed on the machine to check, run the following command to receive a report:
Get-SpeculationControlSettings
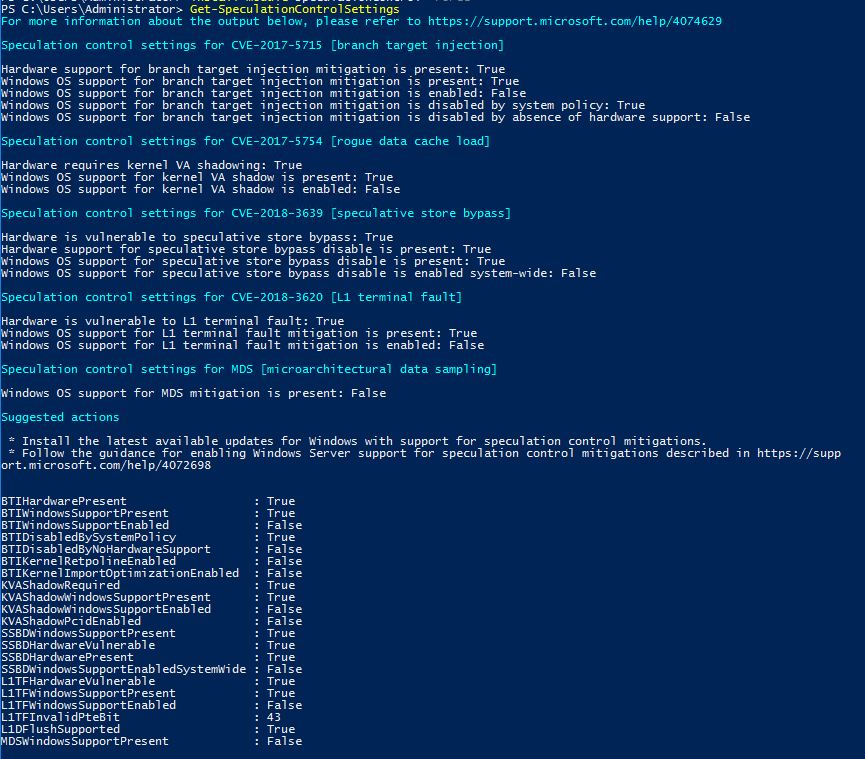
In the screenshot above, there are several patches required to squash these vulnerabilities. As an MSP, manually running this against each client device would take hours and hours. Thankfully we can use PowerShell Remoting to script this out. Copy the following to a notepad and save it as a .PS1:
[CmdletBinding()]
param (
[parameter(Mandatory=$true,Position=0)]
[string[]]$computer,
[parameter(Mandatory=$true,Position=1)]
[pscredential]$credential
)
$report =@()
Foreach($computer in $computers ){
$status = Invoke-Command -ComputerName $computer -ScriptBlock{
Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Force | out-null
Install-Module -Name SpeculationControl -force | out-null
Get-SpeculationControlSettings
} -Credential $credential
$report += $status
}
$report
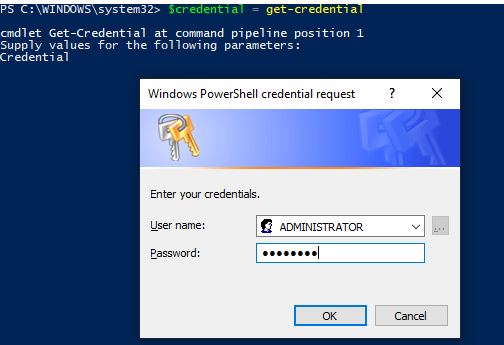
Now, we can open up an administrative command prompt, save the credentials to a variable, we will use this to pass through the script parameter. This credential must have access to the devices we want to run this script against. So for a bunch of devices on a domain, you could input the domain admin credentials:
$credential = get-credential
Now that we have our credentials, we need a list of computers to run against. If you have a lot of devices, you could make a list in a notepad and then grab the contents of the text file using Get-Content cmdlets. However, in this example I’m just going to create a list by using comma separated strings:
$computers = "192.168.0.13","192.168.0.15"
![]()
Now that we have the two variables for our required parameters, we can run our script by simply typing out the path to our .PS1 file in an administrative PowerShell console. Type in the following syntax using both variables:
C:\Scripts\SpeculationControlRemote.ps1 -Computer $computers -Credential $credential
![]()
Each device will install the PowerShell package manager NuGet if it doesn’t already have it, then install the SpeculationControl module from the PowerShell Gallery and run the command to create the report. We get a nice output like the following with the PSComputerName property to distinguish each node:
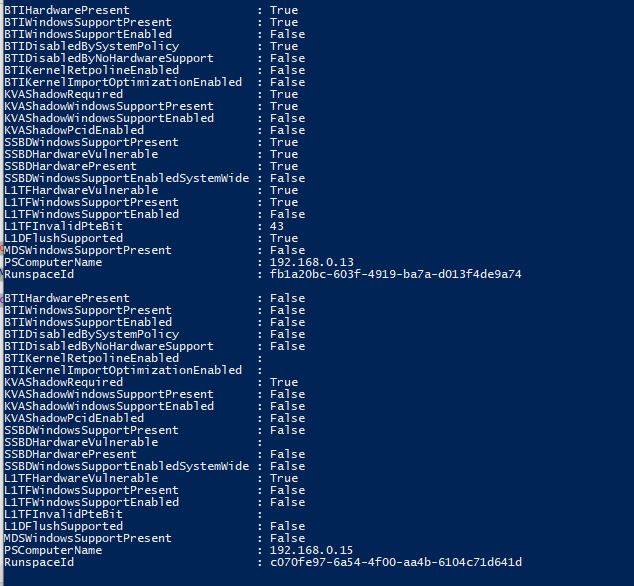
This can be extremely useful for providing a report to a client for assurance that their systems are completely patched and taken care of.
Recommended Actions for Managed Service Providers
With the evolution of IT, we are starting to see the same song and dance each year where a new vulnerability comes out and IT Pros must spend hours patching them. For Managed Service Providers this is a great situation to show clients the worth of hiring an MSP to manage and protect their IT environment so they don’t have to hassle with issues like this. Take the time to educate clients on the vulnerability and the risks associated. Then explain to them the work involved so they can see the value of what they are paying for. I highly recommend taking the next week or two to test out each vendor patches before rolling them out into production, especially for clients. Last year there were bugs in some of the patches for Meltdown and Spectre so we should be cautious in the beginning. From a cost and profitability perspective of running an MSP, the more time and maintenance a client’s environment requires, the more engineering resources they consume which means less overall profitability. Because of this, taking the time to automate the vulnerability patching for each customer can become a huge cost saver. It’s only a matter of time until the next security vulnerability is discovered and we’ll have to do this again, so automate the remediation steps as much as possible.
What about you? Did you have good success patching the spectre vulnerabilities last year? Do you expect this one to create some challenges? If so what challenges do you foresee? Let us know in the comments section below!
Thanks for reading!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









