Save to My DOJO
Table of contents
Do you currently use the same TV, phone, movie player, music player or computer that you had 30 years ago? Probably not, since it would be slow, unsecure, and not designed for today’s highly-connected society. Would it surprise you that many companies are still using a network communication protocol that was designed at the same time? If you or your clients are using Server Message Block version 1 (SMB1), turn it off and replace it! Just like your VHS player, SMB1 is also outdated and not designed for the modern Internet, making it highly vulnerable to attacks. In fact, Microsoft has explicitly warned its users against using it since 2017 and has stopped developed any services that depend on it since 2014. If you are a managed service provider (MSP) then part of your responsibility should be to protect your clients, so you need to take this recommendation seriously, patch any vulnerabilities, and bring your customers to the modern era. This blog will help you understand why SMB1 is unsafe, how to detect if it is still being used, and show you ways to mitigate the risks.
Understanding the Server Message Block (SMB) Protocol
The first Server Message Block (SMB) networking protocol, also known as the Common Internet File System (CIFS), was designed in the mid-1980s by IBM, and first adopted by Microsoft in the early 1990s as part of its LAN Manager products. SMB is an application and presentation layer protocol which is used by organizations to share files, printers, ports and other resources. A fundamental problem with SMB version 1 (SMB1) is that it offers no native encryption. This means that a malicious user with a password can see the messages on the network in plain text, giving them the ability to alter the communications sent between servers. They can steal information, reroute traffic to their own servers, crash a server, or inject code which could execute remotely and take control of a machine. Since most networking hardware manufacturers use default passwords, it became easy for bad actors to hijack network traffic from organizations that did not change their passwords.
Microsoft introduced SMB2 in 2006 with Windows Vista / Windows Server 2008 which supported features like larger block sizes, request compounding, caching of properties, durable handles, security signing, greater scalability, symbolic links, and more. In Windows 8 / Windows Server 2012, Microsoft released SMB3 which enabled many new distributed computing scenarios, such as cluster support, transparent failover, SMB direct, directory leasing, network multichannel, and finally native encryption. SMB2 and SMB3 are designed for the modern era and should be used instead of SMB1.
SMB Version 1 Security Vulnerabilities Leaked
In early 2017, the urgency to drop SMB1 became dire as a new series of cyber attacks were exploiting its vulnerabilities. It turned out the National Security Agency (NSA), one of America’s most trusted government organizations, had discovered several critical weaknesses in SMB1 but decided not to report them to Microsoft or other vendors. The NSA was then hacked by a group which leaked dozens of these exploits, and new classes of malware and ransomware began appearing. These vulnerabilities could create kernel pool corruption which would crash servers, or even allow remote code execution (RCE), which effectively let a malicious user take over a server or computer. Some of the most notorious ransomware which used these SMB1 vulnerabilities included WannaCry, NotPetya, Retefe, and EternalBlue, and they have been estimated to have cost businesses billions of dollars in damages.
These vulnerabilities are documented here:
Microsoft publicly criticized the NSA and US Government for its practice of “stockpiling vulnerabilities” which they claimed the government had intended to use for their own benefit. Microsoft says that if the authorities had disclosed these issues to Microsoft in advance, then they could have proactively started patching SMB1 clients before the hackers began exploiting its weaknesses.
Is your Customer using SMB Version 1?
Microsoft has been campaigning their partners and customer to stop using SMB1. They have even challenged many of the top ISVs and IHVs to stop using it by listing vendors still using SMB1, including Apple, Aruba, ASUS, barracuda, Belkin, Bitdefender, Canon, Cisco, Citrix, Dell / EMC, F5, Fujitsu, Hitachi, HP, IBM, Linksys, Linux Kernel, McAfee, NetApp, NetGear, NVIDIA, Oracle, RedHat, Sony, SUSE, Tintri, Toshiba, VMware and Western Digital.
The following section shows a few ways to check if your customer is still using SMB1 so that you can disable it, as documented in Microsoft Knowledge Base Article 2696547. Be aware that after turning off SMB1, a restart of the operating system will usually be required.
Disabling SMB Version 1 on Windows Server
From Server Manager, you can view the list of features which are installed to determine if “SMB 1.0/CIFS File Sharing Support” is installed. From here you can use the “Remove Roles and Features Wizard” to deselect it and remove it from the system.
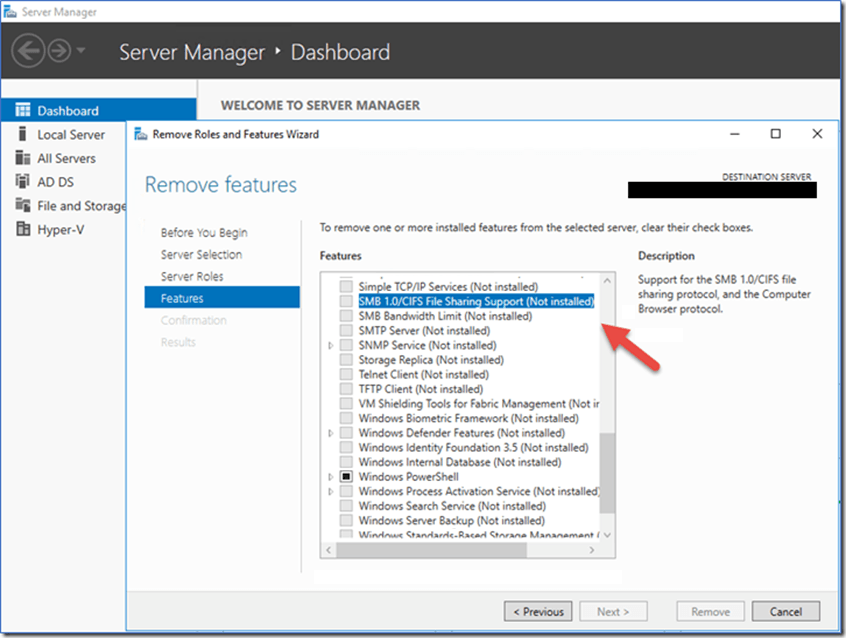
Figure 1: SMB Version 1 on Windows Server
This can also be done through PowerShell using the following cmdlets.
| Detect SMB1 | Get-WindowsFeature FS-SMB1 |
| Disable SMB1 | Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol |
| Enable SMB1 | Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol |
Disabling SMB Version 1 on Windows Client
Checking for and disabling SMB1 is available on Windows client through the “Turn Windows features on or off” interface.
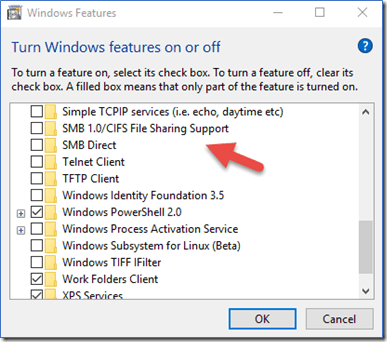
Figure 2 – SMB Version 1 on Windows Client
This can also be done through PowerShell using the following cmdlets.
Disabling SMB Version 1 at Scale
For MSPs working with larger environments, they can use desired state configuration (DSC) to determine if any server or clients in the environment are still using SMB1. These steps are documented in this Microsoft blog by Ralph Kyttle.
The easiest way to disable SMB at scale is through Group Policy, which will globally change the registry setting for any computers using it. These steps are documented in this Microsoft blog by Troy Arwine.
Microsoft Critical Security Bulletin MS17-010
There are some organizations that must continue to use SMB1, for example, if they are still using older (and often unsupported) versions of Windows, their legacy management software relies on this protocol, or their printers have firmware which cannot be updated. If your business is being forced to use this unsafe protocol, then pressure your vendors to update their software to support to SMB2 or SMB3.
If your customers are still stuck with SMB1, then it is critical that you install Microsoft Security Bulletin MS17-010 – Critical. This is a Security Update for servers and clients with following operating systems:
- Client: Windows Vista, Windows 7, Windows 8.1, Windows RT 8.1, Windows 10
- Server (Full and Core installations): Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016
- Older version of Windows client (XP, ME, 2000) and Windows Server (2003) are also vulnerable, but since Microsoft no longer supports these operating systems, there are no public patches available for them. This is a great example of why customers should not use unsupported operating systems like Windows Server 2003. There are rumors that updates are available to some organization who pay for expensive custom support agreements with Microsoft.
You can verify whether this patch has been installed by checking for its KB number, file version, or using PowerShell or WMI. These steps are documented here by Microsoft support.
Now that you understand why using SMB1 is risky, you can appreciate the urgency to upgrade to a newer version as quickly as possible. If you must still use SMB1, but you cannot patch the systems, then make sure that the networks are isolated or they’ll remain vulnerable to ransomware attacks.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









