Save to My DOJO
To say the IT world is changing would be an understatement. On the contrary, it’s changing quicker than it used to, which is common knowledge. But the ramifications of those changes can be hard to perceive when we’re in the middle of the shifting sands.
A few years ago, good firewall systems with content filtering and malware inspection were considered state-of-the-art. Today, you have two problems: first, most of your users aren’t in the office, so they’re not behind that big “blinky light” protector, and second, most of the applications and services your users are accessing aren’t on-premises anymore, they’re cloud services that they access from any device with an internet connection.
No problem, says the older, “pry my servers from my cold, dead hands.” IT Pro, we’ll just force everyone’s traffic back to on-premises via VPN, and then we can inspect all the traffic. Sounds good? Quick question: when your VPN went from 10% of the workforce using it to 100% at the start of 2023 – how was the user experience? And even if that was mitigated, how’s their experience when they’re using Teams / Zoom? Not quite so “modern” anymore?
The point is that security firewalls and filtering need to move with the times, and in this article, we’re going to discuss Cloud Access Security Brokers (CASBs) and, specifically, Microsoft’s Defender for Cloud Apps (MDCA), up until recently known as Microsoft Cloud App Security (MCAS). We’ll also look at how you can use MDCA specifically with Microsoft 365. But first, what is a CASB?
What is a Cloud Access Security Broker (CASB)?
A Cloud Access Security Broker (CASB) emerges as a pivotal player in ensuring the security of cloud-based applications and services. CASBs act as a gatekeeper, mediating between users and cloud service providers to enforce security policies and maintain the integrity of data.
One of the primary roles of a CASB is to enforce security policies. As we migrate to cloud services, traditional on-premises security measures become less effective. CASBs step in to fill this gap by providing security at the cloud level. They ensure that organizational policies regarding data access, sharing, and storage are uniformly applied across all cloud services.
These security solutions offer unparalleled visibility into cloud application usage, allowing you to monitor and control the flow of sensitive information. This visibility is crucial for compliance with various regulatory standards such as GDPR, HIPAA, and SOX. CASBs can identify and classify sensitive data stored in the cloud, monitor its movement, and enforce compliance policies.
CASBs play a vital role in managing who has access to cloud applications and data. They integrate with existing identity management systems to provide secure authentication and Single Sign-On (SSO) capabilities. This ensures that only authorized users can access sensitive cloud resources.
In this context, Microsoft Defender for Cloud Apps, a leading CASB solution, plays a pivotal role in securing cloud environments. It offers comprehensive protection across several dimensions of cloud security. With its advanced capabilities in data protection, threat detection, and seamless integration with various cloud services, it represents a robust solution for managing and securing cloud applications. Defender for Cloud Apps extends its functionality to monitor a wide range of cloud applications, thereby ensuring that organizations have the tools they need to secure their cloud footprint effectively.
With the exponential growth in cloud adoption, the importance of CASBs cannot be overstated. They are not just tools for security; they are essential components of a modern cloud strategy. CASBs bridge the gap between the dynamic nature of cloud services and the need for robust security and compliance. They enable us to harness the power of the cloud while ensuring that data and applications remain secure and compliant with internal and external regulations.
With that said, let’s dive deeper into Microsoft Defender for Cloud Apps and learn more about its potential.
Deploy Microsoft Defender for Cloud Apps
While the new name makes perfect sense, I know I’ll have to deal with numerous questions about the difference between it and Microsoft Defender for Cloud, the new name for Azure Security Center and Azure Defender. Defender for Cloud is all about protecting workloads in Azure (and AWS & GCP, hence the name change from Azure Defender to Defender for Cloud), whereas Defender for Cloud Apps is all about spotting shadow IT, managing SaaS service access by your end-users, and applying policy.
Let’s start with how it works – MDCA needs access to data on what apps your users are browsing on the internet. You can continuously upload logs from your on-premises firewalls and proxy servers, integrate directly with a set of cloud services with API connections, and use Microsoft Defender for Endpoint as an agent for MDCA. The number of cloud services that can be integrated into MDCA is increasing; at the time of writing, they are:
- Atlassian (Preview)
- AWS
- Azure
- Box
- Dropbox
- Egnyte
- GCP
- GitHub Enterprise Cloud
- Google Workspace
- NetDocuments
- Office 365
- Okta
- OneLogin
- Salesforce
- ServiceNow
- Slack
- Smartsheet
- Webex
- Workday
- Zendesk
The list of supported firewalls and proxies is too long to list, but you can find it here. It includes all the usual suspects plus cloud-based “firewalls” such as Zscaler and iboss. You can also use Syslog or FTP with “container appliances” to upload custom logs to MDCA, and you can customize the log parser if you need to.
As mentioned, if you’re using Defender for Endpoint (MDE) Plan 2 on Windows 10/11, it’s an excellent way to gather data for MDCA. Note that while MDE also supports Android, iOS, Linux, and MacOS, they’re not supported as agents for MDCA today, and Defender for Business (in public preview) and Defender for Endpoint Plan 1 (included in Microsoft 365 E3) also aren’t supported.
Since both MDCA and Endpoint Plan 2 are part of Microsoft 365 E5 licensing, this is less of a hurdle than you might think (see flavors below). The steps to integrate them are really simple: a single slider in each portal needs to be enabled.
The power this brings is not to be underestimated; you get a full 360 view of all services accessed by your users, no matter where they’re working and how they’re connecting, and you can apply policies to them.
Shadow IT Discovery
OK, once you have data flowing into Defender for Cloud Apps through any of the methods above, you’ll start getting Cloud Discovery reports. This will tell you what service categories are most used, which apps are most used by your users, and if there’s the usage of high/medium and low-risk apps. Commonly known as shadow IT, this is the usage of apps that the business isn’t aware of, including the potential storage of sensitive data in these locations. It’s vital that this is discovered and managed, and Defender for Cloud Apps helps you a lot with this task.

Defender for Cloud Apps Cloud Discovery dashboard
Based on this data, you can start digging into the riskiest apps with high usage and identify why they’re being used and what the risks are. There’s a built-in catalog of 30,036 apps (and growing; the last time I looked, it was just over 27,000). Each app/cloud service in the catalog has an overall score from 1-10, based on four categories: General, Security, Compliance and Legal.

Defender for Cloud Apps catalog listing
The point of the catalog is to give you instant visibility into the security stance (perhaps of a service you’ve just found out is used by the entire finance department) and regulatory compliance of an app without having to spend hours digging through their website or requesting more information from them. For instance, if your organization requires suppliers to adhere to a specific compliance regulation, you can filter the catalog to identify any application in use that doesn’t.
The next step is to sanction or unsanction an app. The latter will block access if you’re using Defender for Endpoint, Zscaler, or iboss, and there are options to download a script to add the block to on-premises firewalls. But even if you’re not outright blocking the use of these apps, it does allow you to track down the users and suggest an alternative app with a better security track record.
Another way that I find this discovery useful is by letting me find popular apps that I can publish through Azure Active Directory for users to add governance around their usage.
Using Defender for Cloud Apps
You can use several types of policies to detect risky behavior and suspicious activity and, in some cases, automatically remediate the issue.
Activity policies use the APIs of integrated applications and let you build custom alerts for multiple failed sign-ins and large amounts of file downloads or logins from unusual countries or regions. Anomaly detection uses User and Entity Behavioral Analytics (UEBA) and Machine Learning, and for most detections, it takes seven days to establish a baseline so it can identify what’s unusual. Signals used in these policies include risky IP addresses, inactive accounts, locations, devices, user agents, etc.
Malware detection across Box, Dropbox, Google Workspace, and Office 365 (when used with Defender for Office 365) is one of these policies.
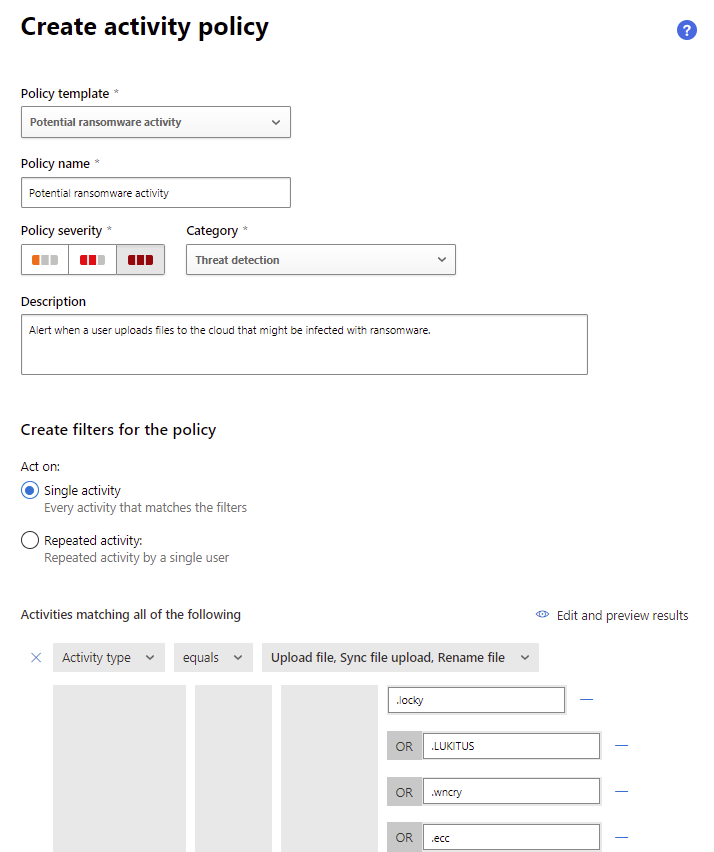
Defender for Cloud Apps activity policy to catch ransomware
OAuth app policies keep an eye on apps that are granted permissions in Azure AD, either by end-users (if you allow this) or by administrators. We covered the risks and mitigations in-depth in an article and webinar.
File policies bring a built-in DLP engine to inspect content across 100+ file types and allow you to take automated action when the content matches your criteria. You can create policies for publicly shared files, files shared with a specific domain or with a specific set of unauthorized users, and even for specific high-risk file extensions.
Access policies are a very cool concept, essentially combining the best of Azure AD Conditional Access policies with the app control of MDAC. You deploy the apps using Conditional Access App Control, and this lets you not only block access to applications based on the user’s device, for instance, but it also allows you to use session policies to control what a user can do in the app. You can monitor all activity, block all downloads, block specific activities, require step-up authentication for sensitive tasks, protect files on download or upload, block malware, and educate users on protecting sensitive files.

Defender for Cloud Apps cloud discovery anomaly detection policy
Finally, App discovery policies alert you to new cloud services that are being used (to continue the fight against Shadow IT), and cloud discovery anomaly detection policies alert you to unusual activity in cloud apps.
Unlike many other security applications, what I like about Defender for Cloud Apps is that it creates many default policies for you “out of the box,” so you’re getting good protection even before you create your own policies.
Alerts from these policies can be sent as emails or text messages, or you can use a Power Automate playbook to notify the right people. You can also automatically disable a user account, require the user to sign in again, or confirm them as compromised to automatically contain a potential attack.
As you can see, you can provide granular control over what your users can and can’t do in cloud applications, and if they’re working from home (on Windows 10/11 devices), they’re still under your purview. Note that it’s not only end-user SaaS services that are protected with Defender for Cloud Apps: AWS, GCP, and Azure admin access and usage can also be monitored and controlled.
The integration with the rest of the Microsoft 365 Defender stack is also strong; here’s an example of a Data Loss Prevention policy being used to control sensitive data in third-party apps.
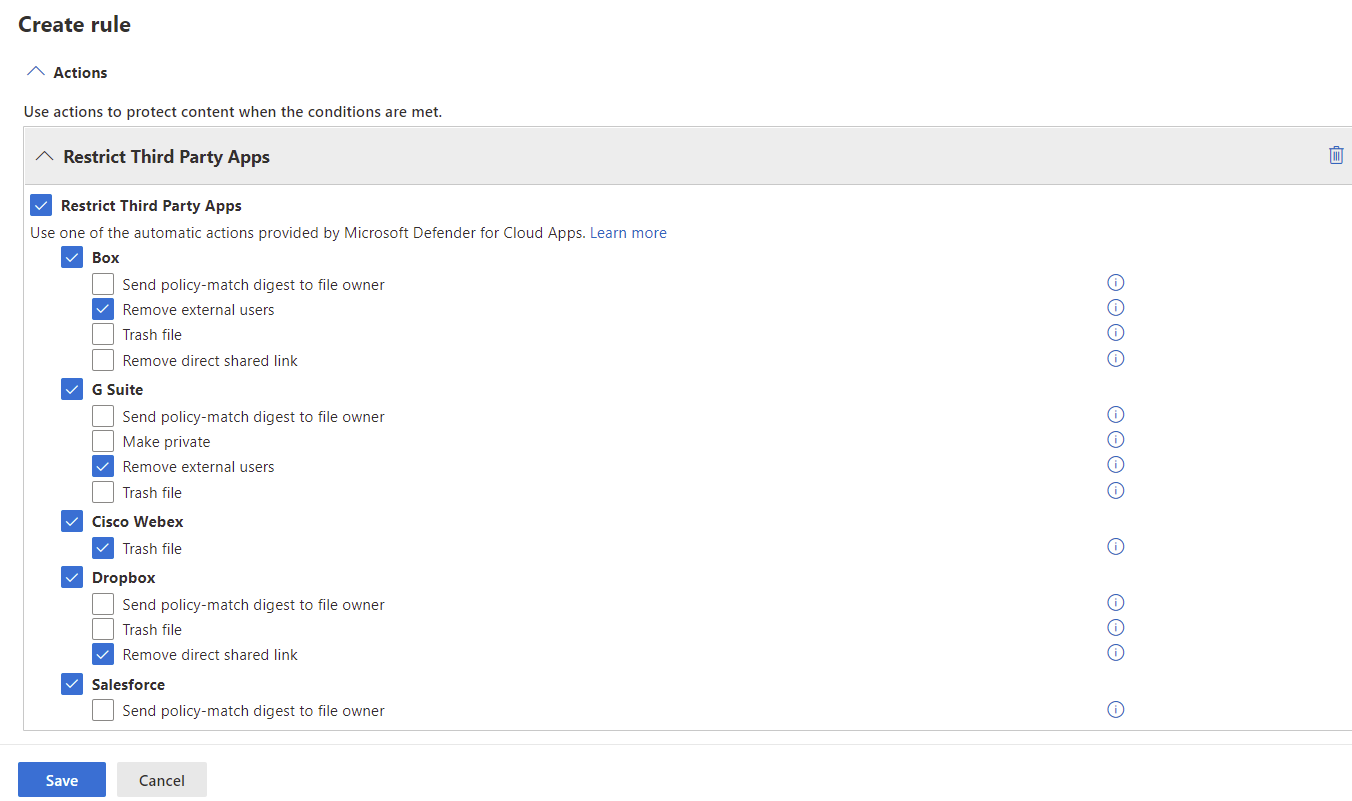
Microsoft 365 Data Loss Prevention Policy integration
Flavors of Defender for Cloud Apps
There are three flavors of Defender for Cloud Apps; the full version we’ve described so far is part of Microsoft 365 E5 licensing (or a stand-alone license). With Office 365 E5, you get Office 365 Cloud App Security, which only has a catalog of about 750 cloud apps (that are similar in functionality to Office 365), only manual upload of firewall logs for analysis, app control, and threat detections for office type apps only and Conditional Access App Control for Office 365 apps only.
On the other hand, Cloud App Discovery is part of Azure Active Directory Premium P1 and brings the full catalog of cloud apps and both manual and automatic log upload but no information protection / DLP or threat detections at all (hence the name “discovery”).
Here’s a deep dive on licensing if you really have trouble going to sleep. Alternatively, I appeared on an episode of the Sysadmin DOJO Podcast discussing this exact topic:
Defender for Cloud Apps for Microsoft 365
There’s quite a steep price jump from Microsoft 365 E3 to E5. Today, if your business collaboration is built on Office 365, digital transformation is the aim of the business, and people are working from anywhere, the power of Defender for Cloud Apps, with Defender for Endpoint as the agent, makes it a lot easier to convince the bean counters.
If you’re an MSP and have clients with strong security and compliance needs (financial industry, lawyers, medical facilities, etc.), even if they’re an SMB, consider upgrading to E5. This doesn’t just give you Defender for Cloud Apps; it also offers Defender for Identity along with a whole heap of other security features.
To properly protect your Hyper-V virtual machines, use Altaro VM Backup to backup and replicate your virtual machines securely. We work hard perpetually to give our customers confidence in their Hyper-V backup strategy.
To keep up to date with the latest Hyper-V best practices, become a member of the Hyper-V DOJO now (it’s free).
Conclusion
As you can tell, Defender for Cloud Apps is a powerful tool with numerous uses. Its comprehensive features, ranging from shadow IT detection to robust policy enforcement and integration with a broad spectrum of cloud services, make it an indispensable asset for any organization leveraging cloud technology.
This solution not only enhances security but also streamlines compliance, offering a seamless blend of protection and convenience. The versatility of Defender for Cloud Apps is further underscored by its adaptability across various cloud environments, including AWS, GCP, and Azure. This adaptability ensures that businesses can maintain a high security posture while embracing the flexibility of cloud services.
To learn more, visit the Ninja training page (each Microsoft security product has one), which is a set of links to webinars, docs pages, blog articles, interactive guides, product videos, and GitHub repositories.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!