Save to My DOJO
It’s on the evening news, in your social media, in nearly every vendor presentation you attend, and the theme of most large IT conferences – security. And the security threats to M365 have never been larger. Luckily, Hornetsecurity’s Cyber Security Report 2024 is now out and contains cutting-edge research on the most critical M365 security.
In this article, we’ll look at the main takeaways and cyber risk management steps you should implement in your tenant to combat email threats and reduce your chances of ending up on front page news (for the wrong reasons).
If you’re in a large corporation with supportive executives and a clear mandate to improve your cyber resilience, you probably know exactly what steps you need to take. For the rest of us, whether you’re in a large or small business, the huge wave of security advice for the cyber threat landscape can be hard to surf (apologies for the Aussie reference). What do you do first? What’s going to give you the most resilience against cybersecurity threats?
Here are the four major takeaways from the Cyber Security Report 2024.
Email threats – still the primary vector
Let’s start by looking at different types of email security threats. Regular spam entices you to buy something, and then there’s phishing. This type of attack relies on social engineering to trick the user into clicking on a link, entering their username and password into a fake login page, or opening an attachment they shouldn’t. Variants include smishing in SMS/text messages, vishing in voice messages or calls, and spear phishing, a specially crafted, targeted email threat that lures specifically for particular recipients.
Another type of email security threat, which poses a significant risk to businesses, is Business Email Compromise (BEC), which also relies on social engineering to trick users, but here, the criminal is inserting themselves into a legitimate email conversation thread and (for example) at the right time, sends an email advising that a bank account number has changed for the upcoming transaction, of course leading to the criminal’s bank account.
Spoofing is often a part of these attacks where the email looks like it’s coming from a trusted or known sender, but there are slight changes to domain names or sender display names that’ll fool a casual observer. Overall estimates (criminals don’t submit financial reports) say that BEC losses worldwide are actually outstripping ransomware costs.
The final category of email threats is malware delivery, either directly as an attachment or tricking the user into clicking a link to download the malware, often leading to system compromise.
Here’s an example of an email threat malware attack, covered in depth in the Cyber Security Report 2024.

A Growing Industry
The days of a group of hackers performing every step of a compromise are long gone. Today, the cybercriminal marketplace has evolved into specialization, where each group completes a single step and then sells that to the highest bidder. So, you don’t write your own access tools; someone else does, and you buy it from them (or rent, and they take a cut from your “earnings”). You also procure a ransomware kit from someone else.
Perhaps you buy access to a victim organization from an Initial Access Broker (IAB). In this gig economy of criminality, you don’t get the whole pie for yourself, but the overall efficiency is improved because everyone is focused on their link in the chain. And the barrier to entry is lowered considerably, inviting more players into this burgeoning “industry” of data breaches.
Also, with the move to “big game” ransomware attacks where payouts in millions of dollars aren’t unheard of, expect the criminals to do their homework on sites such as LinkedIn and ZoomInfo – they’ll know exactly what you can afford to pay once they spring their trap. And they’ll focus on targets most likely to pay, such as hospitals and critical infrastructure, whose function in society will increase the pressure to pay. Some are even state-sponsored ransomware attacks, which are generally harder to defend against.
IABs has a few different ways to gain access to your organization. They might buy credentials from a data breach and try matching emails/passwords against your Microsoft 365 tenant; it’s no secret that most users re-use their “favorite” password across personal and business accounts. Your best protection here is MFA – preferably a phishing-resistant flavor such as FIDO2 key or Windows Hello for Business. Also, block commonly used passwords using Password Protection in Azure AD / Active Directory.
But as the report reveals, the preferred way of compromising patient zero is through Phishing. Nearly 5% of all emails in our data (25 billion emails over the year) are classified as malicious, and 40% of attacks involving emails are phishing. Send a specially crafted email to the user with an enticing attachment or an important-looking link in the email itself, and wait for the users to do your work for you. Once they enter the credentials on a fake Microsoft 365 login page (this is why you should customize backgrounds and logos so that users are more likely to stop and think when the login page doesn’t look familiar) or open the malware-laden attachment, it usually only takes minutes before the criminals use the access.
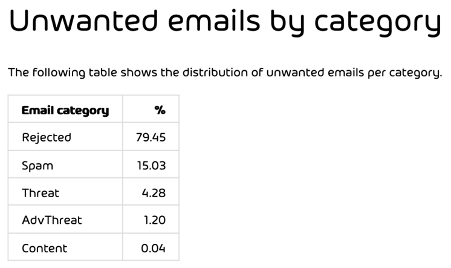
By now, it should be obvious that you need a strong and easy-to-use email hygiene solution to keep your organization and your sensitive data safe from cybersecurity threats such as 365 Total Protection. But technology alone isn’t enough to combat email threats; you need to improve your “human firewalls” by training your users, another conclusion we made in the Cyber Security Report 2023.
The combination of well-trained people, secure processes (call to check with the person in the other company whenever a bank account number is altered, for example), and technology creates a cyber-resilient business. You can’t combat many cyber threats individually, but you can increase your organization’s overall security defenses by combining people, processes, and technology.
We also found that brand impersonation is very common in email threats. Users are much more likely to fall for a phishing attack if the email looks legitimate, with all the right logos and text. Cyber security vulnerabilities aren’t just about technical flaws; they’re just as much about psychology and creating the right approach and culture to manage cyber risk.
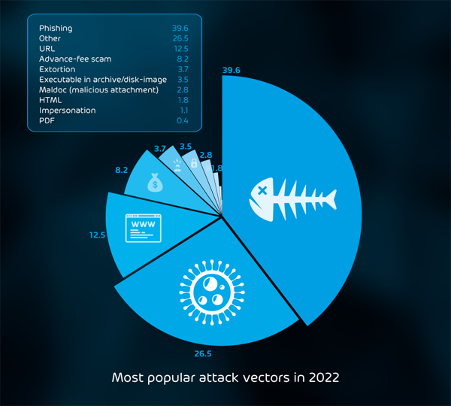
Beyond Email Threats
A growing attack vector is phishing and other cybersecurity threats spreading beyond emails. The mantra for years (in the Microsoft world) has been to move internal and external collaboration into Microsoft Teams. We see attacks increasing, particularly as it’s getting easier to collaborate with users outside your business in Teams.
Speaking of Teams, we also noted that the desktop app itself has some security implications as it runs as an Electron app and recommends that users stick with the web version instead, as all of the modern security enhancements in browsers protect you.
A worrying trend is the shortening of exploit timelines. The gap between a cyber security vulnerability being publicly disclosed and attacks against your users and system has shortened considerably in the last few years. This increases the pressure on already strained security teams to prioritize the right systems to patch based on the level of cyber risk in your particular context. A hospital or a school will have different systems and priorities compared to a critical infrastructure provider, which will affect their security posture.
Another interesting finding in the report was the impression some IT staff have that “if it’s in the cloud, it’s secure.” Nearly 25% of staff were either unsure or thought that Microsoft 365 was immune to ransomware attacks, which it’s not. In the shared responsibility model from Microsoft (and any other cloud provider), you are responsible for your data, endpoints, and identity governance as part of your overall cyber risk management. A good backup solution for Microsoft 365 (including Teams data) is a must to protect against data loss and ransomware.
A Strong Defense
There are several layers in protecting against email security threats. For any email system, ensure that your Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) DNS records are in place and correct. Collectively, these records help your email hygiene solutions to spot incoming spam and filter out phishing scams and spoofed email threats.
A good email hygiene solution should integrate seamlessly with Exchange Online. For any email threat that does slip through, frequent and easy-to-digest user awareness training and simulated phishing attacks increase the resiliency of your end users against falling for the threat actor’s tricks.
Finally, if an email threat gets through these layers and starts a compromise or attack, a good backup solution for all your critical data gives you a way to recover, should it be necessary.
Read the Full Report
In this article, we’ve only scratched the surface of the Cyber Security Report 2024 and what you should do about email security threats to increase your security posture. The full report goes deep into the statistics cyber risk, and also covers other predictions and advice for time-poor IT and security staff. Enjoy reading it!



Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









