Save to My DOJO
In this post, you’ll get a short introduction to Azure Bastion Host. To be honest, I still don’t know if I should pronounce it as [basˈti̯oːn] (German), /bæstʃən/ (US engl.) or [basˈt̪jõn] (french) but that shouldn’t stop us from learning more about Azure Bastion Host, what is it, and when it’s useful.
We will also discuss a webinar on Azure Security Center.
So let’s start.
What is a bastion host?
In general, a cloud bastion host is a special-purpose host that provides connectivity to internal servers in cloud networks without exposing these internal servers to the Internet with public addresses. Bastion hosts can be configured in such a way they act as “jump boxes” for certain types of traffic, including SSH and RDP.
What is Azure Bastion Host?
Azure Bastion Host is a Jump-server as a Service within an Azure vNet. What does that mean exactly? Well, a jump server is a fixed point on a network that is the sole place for you to remote in, get to other servers and services, and manage the environment through bastion in Azure. Now some will say, but I build my own jump server VM myself! While you’re certainly free to do that yourself, there are some key differences between the self-built VM option and the Azure Bastion service.
A regular Jump-server VM must either be reachable via VPN or needs to have a public IP with RDP and/or SSH open to the Internet. Option one, in some environments, is rather complex. Option two is a security nightmare. With Azure Bastion Host, you can solve this access issue. The Azure Bastion service enables you to use RDP and SSH via the Internet or (if available) via a VPN using the Azure Portal. The VM does not need a public IP, which GREATLY increases security for the target machine.
NOTE: Looking for more great content on security? Watch our webinar on Azure Security Center On-Demand.
After the deployment (which we’ll talk about in a second), the Azure Bastion host becomes the 3rd option when connecting to a VM through the Azure Portal, as shown below.
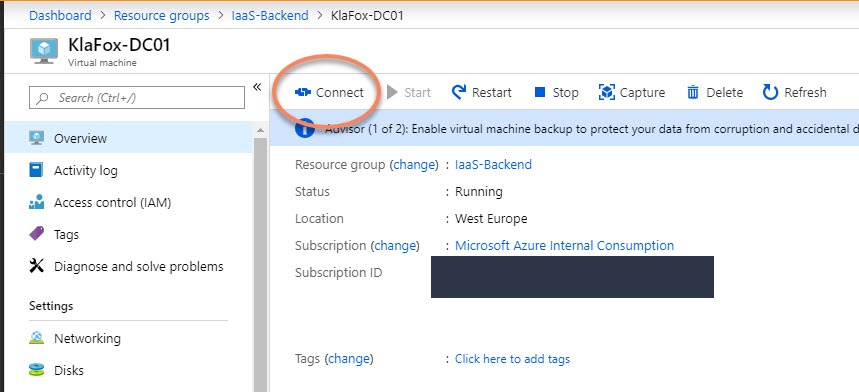
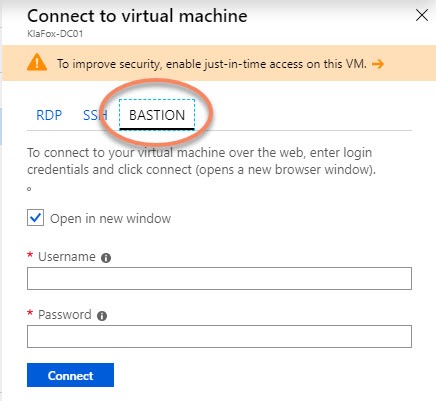
After you hit connect, a HTTPs browser Window will open and your session will open within an SSL encrypted Window.
Azure Bastion Use Cases
Now let’s list some possible use-cases. Azure Bastion can be very useful (but not limited) to these scenarios:
-
- Your Azure-based VMs are running in a subscription where you’re unable to connect via VPN, and for security reasons, you cannot set up a dedicated Jump-host within that vNet.
- The usage of a Jump-host or Terminal Server in Azure would be more cost-intensive than using a Bastion Host within the VNet (e.g. when you have more than one admin or user working on the host at the same time.)
- You want to give developers access to a single VM without giving them access to additional services like a VPN or other things running within the VNet.
- You want to implement Just in Time (JIT) Administration in Azure. You can deploy and enable Bastion Host on the fly and as you need it. This allows you to implement it as part of your Operating System Runbook when you need to maintain the OS of an Azure-based VM. The Azure Bastion host allows you to do this without setting up permanent access to the VM.
How to deploy Azure Bastion to protect VM environments
The way you deploy Azure Bastion Host within a VNet is pretty straightforward. Let’s go through the Azure Bastion setup steps together.
-
-
- Open the Azure Preview Portal through the following link.
- Search for the feature in the Azure Marketplace and walk through the deployment wizard by filling out the fields shown below.
-
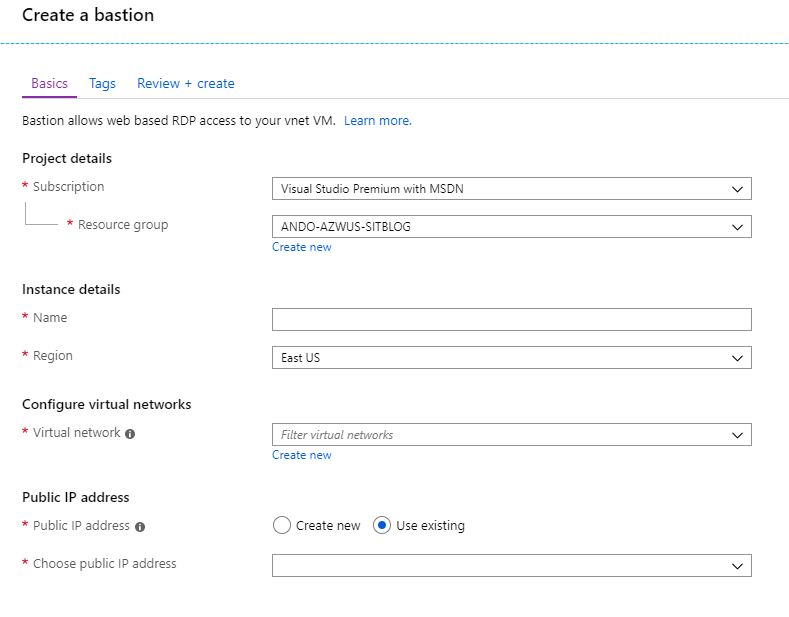
Again, the Bastion host Azure deployment is quite simple and most options are fairly well explained within the UI. However, if you want further details, you can find them in the official feature documentation here.
Also, be aware that a Bastion Host must be implemented in every vNet where you want to connect to a VM. Currently, Bastion does not support vNet Peering.
How Much Does Azure Bastion Cost?
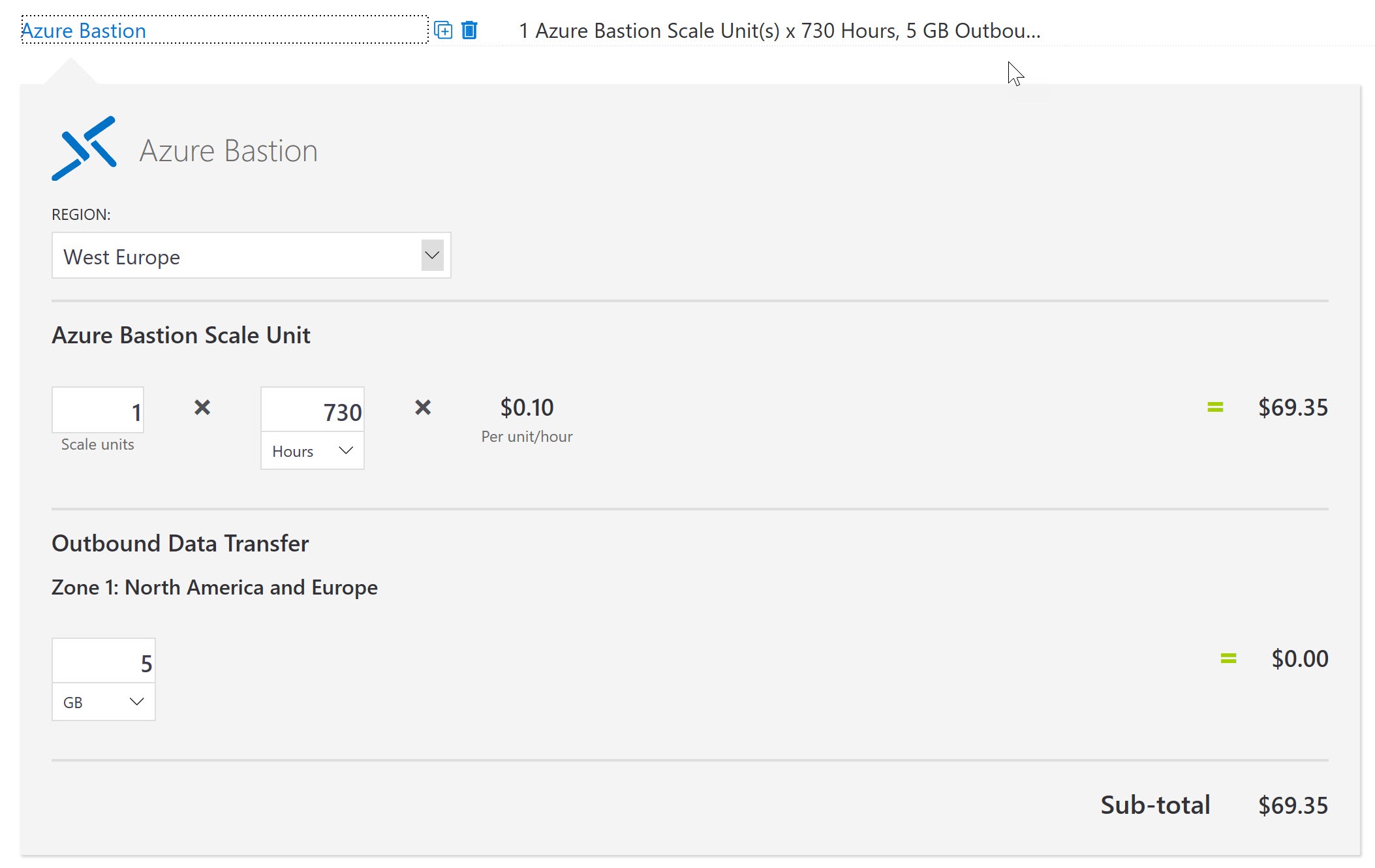
Pricing for Bastion is pretty easy to understand. As with all Microsoft VM Services, you pay for the time the Bastion host is deployed and for any Bastion service you have deployed. You can easily calculate the costs for the Bastions Hosts you need via Azure Price Calculator.
I made my example for one Bastion Host in West Europe, with the assumption it would be needed all month long.
Bastion Roadmap Items
Being in preview there are still a number of things that Microsoft is adding to Bastion’s feature set. This includes things like:
-
- Single-Sign-On with Azure AD
- Multi-Factor Auth
A much-requested feature, the ability to have a single Bastion and still manage VMs in peered VNets is now available.
You can see additional feature requests or submit your own via the Microsoft Feedback Forum.
If you like a feature request or want to push your own request, keep an eye on the votes. The more votes a piece of feedback has, the more likely Microsoft will work on the feature.
Additional Documentation and Wrap-Up
Additional documentation can be found on the Azure Bastion Sales Page.
Finally, if you’re interested in learning more about Azure security issues why not watch our webinar session on Azure Security Center? Presented by Thomas Maurer from the Azure Engineering Team, the free on-demand webinar Azure Security Center: How to Protect your Datacenter with Next Generation Security explains all about this important security package and how you should be using it to ensure your Azure ecosystem is fully protected! This webinar originally aired on July 30th, 2019 but is available to watch free on-demand right now!
The following section details the full question list asked during the webinar and their answers from Thomas Maurer.
Webinar &A
Q: Question about Windows Events where Thomas talked about where the Security Center gets his information from. How about logs that are been overwritten within the VM, will those logs also be stored, or will it be showed ones?
A: The logs which are sent do Azure Log Analytics are not overwritten if the logs on the Windows Server are overwritten.
Q: Do you think that Security Center Standard will ever be able to enable per specific VMs within the same subscription. A lot of my clients don’t want to enable it on all their VMs? (I know that sounds crazy, but costs do come into it most of the time)
A: Currently, Azure Security Center Standard is enabled per subscription.
Q: Is Security Centre only useful for VMs? If you only use Azure Web Apps, is it relevant?
A: Yes, Azure Security Center does not only help protect VM workloads it also helps you to protect your PaaS services like WebApps and SQL.
Q: We are an MSP – can security center be run over multi customers?
A: Yes, with the announcement of Azure Lighthouse, Security Center can be used over multiple Tenant.
Q: If this is constantly scanning all infrastructure for security issues, how does MS recommend we plan for the additional resources needed to support this scanning activity?
A: The most impactful scanning is happing on the Azure Infrastructure. Read more information on Data collection.
Q: When can we export to CSV from ASC?
A: This is a highly requested feature which may enter into development soon.
Q: What is the reasonable security score to keep? 100 out of 100 is not possible all the time, for example, if I do not want to have just in time VM access and pay for standard…
A: Higher is always better. However, it really depends on the customer and the environment. In a closed Sandbox environment you might don’t want or can’t follow all the recommendations.
Q: can we include Governance in the security center ?
A: Yes Azure Policy is integrated in Azure Security Center and Security Center check for Policies which are not matched.
Q: Hi…can we send syslog messages from Azure security center to third party shells server?
A: Yes you can trigger Azure Security Center Playbooks based on Azure Logic App, to automate tasks like this.
Q: Any idea how the security center will integrate with Azure Sentinel going forward?
A: You can connect Azure Security Center to Azure Sentinel
Q: There are Security Center Policies and native Azure Policies, how these play together and what’s the best way to manage? Thx.
A: Yes
Q: How can we monitor who accessed port 3389 witihin the Security Center? (as soon as JIT is enabled)
A: JIT logs all the requests for access. You can also use Network Watcher to monitor network communication between virtual machines.
Q: In addition to the price, management also looks for the “resources time” to implement and operate. Is there some customers examples on how much resource it takes for implementation and/or operations? Is this a task to be added to existing sec/ops teams?
A: Fully depends on the customer and environment
Q: Sorry if this is a bit of a dumb question, but I’m a sales guy from an on-prem background. Is something like JIT VM access only relevant/available with Azure services or might it also be relevant in traditional on-prem environments?
A: Azure JIT VM access is only for Azure VMs, however there are other solutions like PowerShell JIT and other concepts to do similar things.
Q: Hi, for RDP access to VM’s within Azure would you recommend a virtual ‘jump box’ and just in time access. The jump box would be allowed access internally to the live VM’s for that Live service?
A: A jumpbox is one option, but you can also have a look at <the focus of this blog post> Azure Bastion
Q: Which Agents required to install on local VMs when I want to manage in Azure security center?
A: Yes
Q: Is there another interface/portal available for users to request JIT access? ie if you want to provide user access to the new Azure VDI services, can you secure this with Security Centre, and then provide a mechanism for users to request access dynamically?
A: If you are looking at a VDI services you might want to have a look at Windows Virtual Desktops, if it is for Admin Access Azure Bastion (Currently in Preview) will be a good option
Q: I personally find some security recommendations as a money making strategy from Microsoft. For example, in my Azure environment, I have virtual machines that have Premium Managed disk, which I believe has a strong encryption but Microsoft recommended that I should apply Disk encryption such as Bit-locker and the severity level is classified as critical.
I know and understand that it adds an extra layer of security but is it really necessary to address the finding? How strong is disk managed encryption? May you please share your view on this finding?
A: You always need to define by yourself if the recommendation is recommended for you and your environment. For the disk example, Azure encrypts data at rest, however Virtual Disks are not encrypted by default. With Bitlocker you get another level of protection.
Q: Are there any recomendations in the security center to move webapps to separate subnets based on their traffic?
A: Recommendations are updated a lot, but not all recommendations are always integrated. Check these security recommendations in Azure App Service.
Q: Can we replicate all logs from Security Center to on-prem or storage blob?
A: Security Center can be connected to different SIEM solutions like Azure Sentinal. You can also build your own expert tool to export data. Learn more about Log queries: https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/log-query-overview?WT.mc_id=altaro-blog-thmaure
Q: You mentioned that traffic to and from webapps is monitored to be used with ML. Is this kind of information (graphs) availabe in the security center or somewhere else?
A: You can find more information about Network resource protection in Azure Security Center here: https://docs.microsoft.com/en-us/azure/security-center/security-center-network-recommendations?WT.mc_id=altaro-blog-thmaure
Q: There’s always a trade-off… The best security in the world is always going to be the most expensive! Well, unless you’re already the best security engineer 😉
A: true
Q: What about system center with azure security center?
A: I think currently there is no native integration between the two. However, customers can create their own Management packs and Security Center Playbooks to integrate the both.
Q: Where does Azure Sentinel fit into what ASC does? Where do they overlap? What items are unique to each?
A: You can connect Azure Security Center to Azure Sentinel: https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center?WT.mc_id=altaro-blog-thmaure
Q: This is the backend access. How does the user access the request?
A: If you are looking at a VDI services you might want to have a look at Windows Virtual Desktops https://azure.microsoft.com/en-us/services/virtual-desktop?WT.mc_id=altaro-blog-thmaure, if it is for Admin Access Azure Bastion (Currently in Preview) will be a good option.
Q: can JIT access be automated via Service now?
A: I am not aware of an official integration, but using the Azure APIs you could definitely build it by yourself.
To properly protect your Hyper-V virtual machines, use Altaro VM Backup to securely backup and replicate your virtual machines. We work hard perpetually to give our customers confidence in their Hyper-V backup strategy.
To keep up to date with the latest Hyper-V best practices, become a member of the Altaro DOJO | Hyper-V now (it’s free).
Conclusion
Finally, I’d like to wrap up by finding out what you think of Azure Bastion and Azure Security Center. Do you think Azure Bastion is a worthy feature? Is this something that you’ll be putting into production once the feature is out of preview? Any issues you currently see with it today? What about Azure Security Center? Let us know in the comments section below what you think of Azure Bastion.
Thanks for reading!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!










8 thoughts on "What is Azure Bastion?"
What is the advantage of this over a secured RDS gateway? It actually sounds like this is exactly what this is with a new name.
You know what would be very cool to see is a multi-tenant RDS gateway. One which uses one gateway farm but can have discreet customized portals for each tenant/client. I know this would take money out of Microsoft ravenous mouth, but there must be a hack for this somewhere.
Currently the service is very basic, it will get more features down the road.
It is planed as an easy to install and use managed jump server with no need to patch and update.
It is also a bit cheapter than a tradition RDS Web Gateway Server.