Save to My DOJO
Table of contents
As with all infrastructure software, it is critical to stay abreast of updates applicable to Hyper-V. If you’ve got a particular Hyper-V issue and want to know if there’s a hotfix, or if you like to know the intricate details of each and every patch prior to deploying on your system, you’re in luck: Microsoft maintains a complete list of all updates to Hyper-V. The list can be automatically synchronized to your computer via the “Subscribe to Article (RSS)” link on the right side. If you’re on R1, there is a hyperlink in the first “Note” paragraph that will take you to that list. There are also links at the bottom for a similar posting involving Windows Cluster service, if your Hyper-V installation utilizes that technology. The table details the patch number, conditions that make the patch a requirement, what operating system it applies to, and how to get it. Items marked with “hotfix” availability are not included in Windows Update, so you’ll need to manually acquire those if you meet the conditions in the “Required?” column. The “Applies to:” column is actually more important than it might first appear. Obviously, if you’re using Hyper-V R2 then you’re also using Windows Server 2008 R2. However, if you’ve already applied Service Pack 1 to your installation, do not install any hotfixes or patches that are not marked as applying to Windows Server 2008 R2 SP1.
Update Methods
If you require one of the hotfixes, you’ll need to visit the relevant support document which is linked in the first column of the table. That document will contain instructions on obtaining the hotfix. There is no other supported way to obtain a hotfix except waiting for the next Service Pack. Fortunately, most installations won’t need any hotfixes at all. The patches that will be needed on every deployment can be downloaded and installed manually from the Download Center, managed by Windows Server Updates Services, or automatically handled by Windows Update. Your situation will dictate the method that you use.
> Section on Manually installing Patches / Hotfixes on server core & native Hyper-V via command line
> Section on Installing Patches / Hotfixes on server core & native Hyper-V using WSUS
> Section on Installing Patches / Hotfixes on server core & native Hyper-V via Windows Update
Manually Installing Patches / Hotfixes on server core & native Hyper-V via command line
If you like to directly manage the patches for your Hyper-V installation, you can monitor the patch list page from the first paragraph or have it notify you by RSS when there are new Hyper-V patches available. Remember that Windows Server 2008 R2 patches are also applicable and they are not included in this particular list. This method is the most demanding on your time and energy, but may be the only solution in cases involving Hyper-V installations that are completely isolated from any network connection. You’ll need to download the patches from the pages linked from the table; hotfixes may require you to contact support to gain access to the files. After downloading, you must find some way to move the files to your Hyper-V installation, perhaps by copying to a portable USB device or burning to a data CD.
Manual Updates on a Full Installation of Windows (with GUI)
The files are directly readable by Windows. You can just double-click on them and the installation will proceed.
Manual Updates on native Hyper-V or Server Core
.EXE files will run as normal. You’ll need to type their names at the command-prompt to initiate them. Auto-complete can assist. Type the first few characters of the file name and press [TAB] until Windows locates it; you must be in the same folder as the file or have qualified it. For example, if you have placed a file called “patch3.exe” on a USB key in a folder called “patches” and your Hyper-V server treats the USB key as its F: drive, then you can type “F:patchesp” and press [TAB] until it displays “F:patchespatch3.exe” and then press [ENTER]. You can also press [TAB] after entering “F:p” and it will cycle through all folders (and files) on the root of your USB drive that start with “P”.
Most patches will be deployed in a .MSU format. To apply these under native Hyper-V/Server Core, run the following at a command-prompt: “WUSA patchname.MSU /QUIET”. This will install the patch without prompts. It will not notify you if the system needs to be restarted upon completion, so it is advisable to read the patch documentation to see if a reboot is necessary, or simply plan a post-install reboot.
Managing Updates with Windows Server Update Services
Windows Server Update Services (WSUS) is a powerful tool offered by Microsoft at no charge. Its entire feature set is impressive and could easily fill multiple blog posts, so this article will examine only a small subset of its abilities. In this context, its most important feature is fine control over which patches are allowed and when they are installed without requiring administrators to manually perform acquisition and installation. You also gain the ability to download a patch one time for your entire organization, limited bandwidth usage and exposure to tampering. Servers will not need a direct connection to the Internet to get their patches; they only need to be able to contact a WSUS server within your organization. The patches themselves are digitally signed and the entire delivery chain can be contained in SSL, drastically reducing the probability of WSUS being used as a viable attack vector.
The complete setup of WSUS is well beyond the scope of this article, but once you have it configured and running, follow these steps to apply it to your Hyper-V systems:
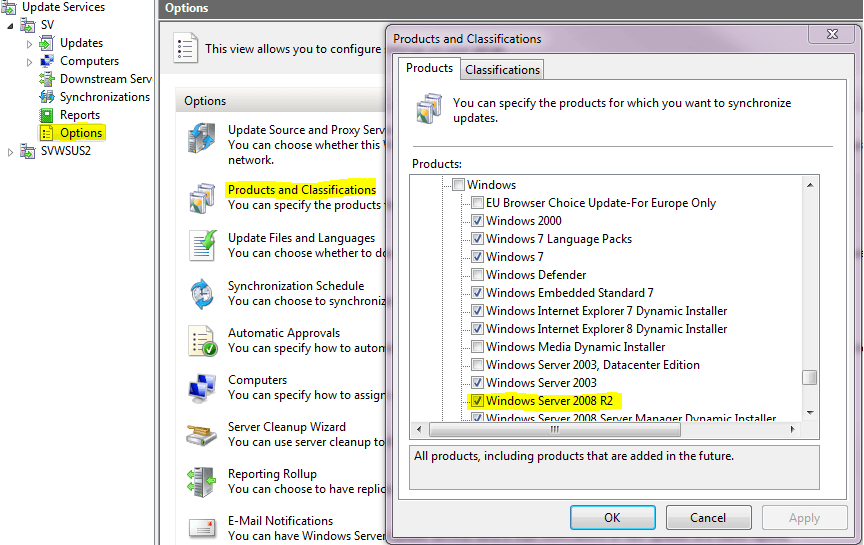
- The first thing is to ensure that your WSUS server is retrieving the proper patches. This is done under Options->Products and Classifications from the main panel. Hyper-V patches are part of Windows Server 2008 (R2), so check that box:
Note that if you’re using Hyper-V R1, you’ll need to select Windows Server 2008, which is a couple of rows below R2. You’ll then need to switch to the Classifications tab in the same box. The items you pick here are only downloaded, not automatically installed, so it is safe to pick “All Classifications”. However, you should at least choose “Critical Updates” and “Security Updates”. Some of the classifications, such as “Definition Updates”, will not apply to Hyper-V at all, but selecting them does no harm.
2. Depending on the size of your organization, this step is optional. If your organization is small enough, you can leave all of your computers in the default “Unassigned Computers” group. All approved patches will then be applied to any applicable computers; you do not need to worry about aligning the products yourself. For instance, if a Windows XP computer is in a group that has some approved Windows 7 patches, it will know not to apply those. In this case, as long as you have followed step 1 and you tell your Hyper-V server(s) about WSUS (covered in subsequent steps), they will automatically apply any relevant patches that you have approved.
3. Before connecting your servers in for updates, you need to decide how those updates will be approved. The simplest way is using Automatic Approvals, which is in the Options section from the picture above. Configuring these are straightforward. For more information about the approval process, see the WSUS documentation.
4. The next goal is to let your Hyper-V server(s) know that WSUS is there and to use it. The easiest, cleanest method to do this is by group policy. The preferred method of utilizing group policy is at the domain level. Domain controllers running Server 2008 and above automatically have the “Group Policy Management” console installed. Windows Vista/7 users can install it as part of RSAT, which is a free download from Microsoft’s Download Center. On Server 2003 and Windows XP, search the Download Center for “Group Policy Management Console”. These tools will connect to a domain controller and allow you to directly edit domain-level group policies. If you are not on a domain or your Hyper-V servers are not part of the domain, you can edit their group policies directly. On a full installation of Windows, just run “gpedit.msc”. For native Hyper-V or Server Core:
a. Open the firewall for remote connectivity (if applicable): netsh advfirewall firewall set rule group=”Remote Administration” new enable=yes
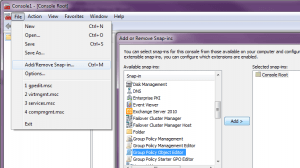
b. Run “mmc.exe” on a Windows computer with a full GUI. Go to File->Add/Remove Snap/In. Under “Available snap-ins, highlight “Group Policy Object Editor” and click “Add >”.
c. This will present another dialog box allowing you to select a computer besides the one you are running the console on. If you simply click finish, it is effectively the same thing as running “gpedit.msc”, except that you will have a console you can modify the settings on. In this case, the goal is to connect to a Hyper-V server. Click “Browse…”, move the selector to “Another computer:” and then enter the computer name manually (IP address is also OK) or, for domain computers, click the “Browse…” button to search the directory. Once you’ve got the computer name or IP, click OK, Finish, and OK.
It is also possible to directly edit the registry on your Hyper-V server and add the WSUS settings. This method is not covered within this article.
5. With whatever method you chose from the previous step, you can now modify group policy on the Hyper-V server to access WSUS. Drill down to Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update. Most of these settings are fairly easy to understand but a full treatment is beyond the scope of this article. The critical components are “Configure Automatic Updates” and “Specify intranet Microsoft update service location”.
a. “Configure Automatic Updates”: This must be set to enabled. You must then choose the degree of automation. “Auto download and notify for install” (option 3) is common and usually the most desirable; it will cause the Hyper-V server to retrieve approved update files but will not install them automatically. If you choose this method on a GUI-less installation, you will need to use another tool to apply and install the patches (SCONFIG.CMD, mentioned later, is already included and is acceptable; Core Configurator is an excellent choice). You must also choose a time for this to occur.
b. “Specify intranet Microsoft update service location”: If you performed the prior step but not this one, your server will retrieve Automatic Updates directly from Microsoft and won’t know anything about which updates you have approved or declined; it will get all available. The address to use in these fields was determined when you installed WSUS.
c. (optional): If you do nothing else, the computer(s) that are affected by this policy will be governed by the WSUS settings for “Unassigned Computers”. If you have created a special group within WSUS, then you need to change the “Enable client-side targeting policy” and enter the name of the group that this computer is to associate with.
d. If you are using domain-level group policy, then the computer will need to be notified of changes. Ordinarily, this will happen within 15 minutes. If you need to hurry that along, run “gpupdate /force” on the computer(s) to receive the change. For all other methods, the changes are instant.
6. All that’s left is to apply the updates. If you have set the process to be completely automated (option 4), then you can simply wait; when the selected time occurs (plus a short, randomized delay), the patches will be downloaded and installed. This could lead to undesirable behavior, since, without other intervention, the server will automatically reboot if a patch requires it and it will take all of its virtual machines with it. If you have set any of the options that include a download, then you can run “wuauclt /detectnow” and it will initiate the download. In a GUI install, you can use the Windows Updates item in the Control Panel or wait for the blue Windows Update icon to appear in the taskbar and manipulate updates that way. In a native Hyper-V or Server Core install, you’ll need to use the aforementioned SCONFIG.CMD, Core Configurator or some other third party tool to manage the installation of downloaded updates.
Fully Automated Patching
This method provides the greatest level of “hands-off” at the greatest loss of convenience. Hyper-V itself receives very few patches, and if the Windows installation in the parent partition has no technical problems and has reasonably hardened, patching it is somewhat optional (please remember to take all due diligence). This means that with some selective managing, your Hyper-V installations will almost never need to be restarted. However, some Hyper-V installations aren’t running anything of significant importance and guest machines aren’t used at all outside business hours. In those cases, the convenience of total automation might outweigh the inconvenience of periodic reboots. In those cases, you can set up Windows Update to work its magic and leave it alone. Note that if the relevant computer is in a domain organizational unit with group policy controls of Windows Update, that policy will supersede everything in this section.
Automation in a GUI Installation
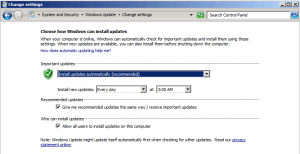
Access the Control Panel under the Start menu. If you are in Categories view, drill down through System and Security to find Windows Update. Click the “Change settings” link at the left. Change “Important Updates” to “Install updates automatically (recommended)”.
This will completely automate the system. In order to start an update now, click OK. It will return to the earlier screen where it will have already started a search for updates:
Upon completion, it will not automatically install these updates. You can wait for it to complete and press the “Install updates” button to continue, or you can just wait for the scheduler to take care of it.
Note that you do not need to select “Get updates for other Microsoft products.” for Hyper-V.
Automation in native Hyper-V R2 or Server Core R2
With Server R2, Microsoft included a scripted server configurator to aid in common configuration tasks. In a native Hyper-V installation, this tool automatically runs at startup. If you’ve closed it or if you’re on Server Core R2, you can manually invoke it from a command-prompt by typing “SCONFIG.CMD”. This will bring you to a text-based menu. To set up fully automated Windows Updates:
- Choose option “5” for “Windows Update Settings”
- Press “a” to set updating to automatic, which will notify you that it will run daily at 3:00 AM.
- After dismissing the dialog, you’ll be returned to the main menu.
- You can exit from here and the scheduler will handle it, or you can press “6” to initiate a download and installation of updates.
- Press “a” if you want all updates or “r” if you only want the recommended updates.
- You will be presented with a list of available updates. You can press “s” to select an individual update, “a” to get all, or “n” to exit back to the prior menu.
Manual Usage of Windows Updates
If you’ve followed along this far, you’ve probably noticed that you can manually invoke Windows Update and only get the items that you need. Checking for updates in the GUI will allow you to pick the updates you wish. Choosing “6 “in SCONFIG.CMD without changing the automatic setting allows you to pick which updates you want and install on demand.
Checking Your Work (or Checking Up on Windows)
If you want to see which updates have been installed, access a command prompt and run “WMIC QFE LIST”. Since this is a WMIC command, it has the ability to format the output which can be redirected to a file as HTML to be used as a report: “WMIC QFE LIST FULL /FORMAT:HTABLE > C:QFE_REPORT.HTM”.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!








4 thoughts on "How to install Microsoft hotfixes / patches on server core & native Hyper-V"
Great article – a huge help for me with running a 10 host / cluster system with hyperv and scvmm.
excellent article!!
MS, We made you what you are today, so keep the windows7 and vista updates coming.