Save to My DOJO
Azure Bastion can be seen as a Jump Host or Secure Admin Station as a service. It allows connecting to Azure Virtual Machines using a secure browser like Google Chrome, Edge, or Firefox via the Azure Portal. In this article, you’ll learn how to set up and run Azure Bastion to provide the optimal level of security for your Virtual Machines. Let’s get to it.
The Azure Bastion Service
Azure Bastion is a Microsoft Azure managed Platform as a Service (PaaS) environment that is deployed inside of Virtual Network. With Azure Bastion, Microsoft provides a seamless and secure RDP and SSH connection directly to a Virtual Machine within the same Virtual Network or Peered Virtual Network. You directly connect from the Azure Portal using TLS to encrypt the traffic.
When you use Azure Bastion, the Virtual Machine within the environment can be encapsulated and does not need any public IP and can be accessed privately. There is also no need for special agents or client software installed on the Virtual Machine. Azure Bastion will relay the https request directly to the RDP or SSH port of the Virtual Machine.
Azure Bastion is deployed within a Microsoft environment and represented to the customer as a single service without exposing the high available infrastructure behind the service.
From an architecture point of view, it looks like shown below.
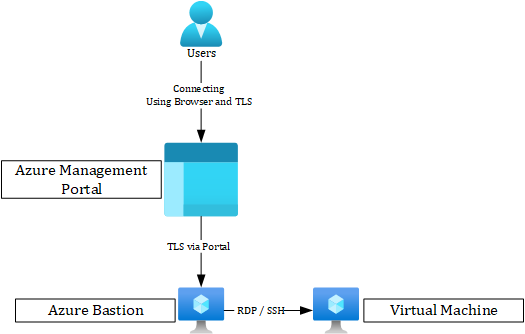
Azure Bastion is a great service, but it does come with its boundaries. Within the next part of the post, I will provide you with more information on that topic.
Benefits and Boundaries of Azure Bastion
As a Platform service, Azure Bastion comes with great benefits but also with its boundaries. I will now provide some information about those.
Benefits
The largest and most beneficial use for Azure Bastion is the enhancement of security. That can be achieved as followed.
With the access of Azure Bastion via the Azure Portal, you can enhance the user experience and security by using Azure Active Directory Features like Multi-Factor Authentication and Conditional Access as well as Azure Role-Based Access Control. When enabling these features, you can enforce users logging into the Portal using Multiple Factors of Authorization, connecting from a trusted device or IP Address. You can also limit the user to only be able to connect to the Virtual Machine using Bastions and do not do any changes in the infrastructure.
To learn more about Azure Active Directory Multi-Factor Authentication, Conditional Access and Role-Based Access Control please follow the links below.
Azure AD Multi-Factor Authentication overview | Microsoft Docs
What is Conditional Access in Azure Active Directory? | Microsoft Docs
Overview of Azure Active Directory role-based access control (RBAC) | Microsoft Docs
The next very important aspect is the Remote Session over TLS. Azure always uses firewall traversal for RDP/SSH and a HTML 5 based web client to connect to the Virtual Machine. As the service is streaming the RDP/SSH session over TLS using port 443 (HTTPs), there are no additional firewall exceptions needed.
Another benefit is that the Azure Virtual Machine does not need any Public IP to connect to. That improves the overall Virtual Machine security. Azure Bastion connects directly to the private IP of the Virtual Machine.
There is another benefit if you use Azure Bastion instead of a Jump Box Virtual Machine. If you ever worked with Network Security Groups in Azure, you know they can become rather complex. If you need to configure a Jump Box, you will have a Virtual Machine Network Security Group to configure. That could be complex and tricky, and by mistake, you may open some ports and with that come security risks.
Azure Bastion also helps to simplify Network Security Group management for your Virtual Machines. In the first place, there is no need to apply any Network Security Group to the Azure Bastion Subnet. The reason is that Azure Bastion connects to your Virtual Machines using a private IP address. On the Subnet or Network Card Network Security Group of your Virtual Machine, you allow only RDP/SSH traffic coming from the Azure Bastion host. With that, you keep the number of exceptions for remote access to a Virtual Machine very limited.
With the limitation of open ports and public IP Addresses on the Subnet and Virtual Machine, a Virtual Machine is fairly protected against scanning and rogue access from malicious users and attackers from outside of your Virtual Network.
When using a Platform as a Service Solution like Azure Bastion, you gain another benefit. As you work with a hardened service, you have no hustle with zero-day exploits like you sometimes have within an Operating System like Windows, Linux etc. Microsoft also keeps the service always up to date and improves the features according to customer feedback.
Boundaries
One of the greatest benefits of Azure Bastion is also its most critical boundary in daily administration work. Azure Bastion acts like HTTPs to RDP/SSH forwarder to the destination machine, which means you don’t have any access to the host itself. But if you are a regular administrator, you most likely have Jump Box with your tools installed, for example, Wireshark, Backup Managed Centers like from Altaro, Windows Admin Center, Putty etc. That is not possible with Azure Bastion, so you need an additional Jump Box or your tools installed on the servers you want to access.
Another downside is majorly an issue for Azure Virtual WAN customers. Currently, Azure Bastion cannot be used to jump from one Virtual Network to another one with the Virtual Machine in, if the Virtual Networks are connected to Virtual WAN.
The third boundary I would at least bring to your attention is the costs. If you run Azure Bastion, it will cost around 45€ per month. If you only use it occasionally there are much more cost-efficient solutions like running a B-Series Virtual Machine with Windows Admin Center on it. I will present the B-Series Solutions as an alternative to Azure Bastion later within this blogpost.
The last boundary I need to mention with Platform as a Service Solutions may already be familiar to you. It is a Platform service with a limited option on customization. If you are lacking features or things are not working for you as they are implemented, you cannot change them. You can provide feedback to Microsoft Product development through the usual channels, but Microsoft needs to have a solid customer base and business value behind to develop such a feature. Such a change also needs to be implementable within the service and needs to follow all security and multi-tenancy requirements of Microsoft.
Use Cases
As you can imagine from the benefits and boundaries of the services, there are some use cases that stand out for using Azure Bastion. I would like to introduce you to two of my preferred use cases.
Just enough and Just in Time administration
My first use case is based on the concept of Just enough Administration (JEA) and Just in Time (JIT) administration.
Just enough Administration limits the number of privileges of an administrator or power user to only that task they need to fulfil. Those tasks could be reset of passwords or server resets. No other tasks are allowed for that user. You can find more information here.
Overview of Just Enough Administration (JEA) – PowerShell | Microsoft Docs
Just in Time Administration allows users only for a limited amount of time. Microsoft also calls it Privileged Identity. If for example support is needed, the necessary support tasks and privileges can be granted to the user, administrator, or partner. Please find more information here.
What is Privileged Identity Management? – Azure AD | Microsoft Docs
These two technologies combined with Azure Role-Based Access control and Bastion, can help you secure and automate access. Let’s think of a common task in daily business. You run a 3rd party application on a Virtual Machine that needs to be supported and maintained by a partner. Your security requires that no one has access to the system if there is no support or maintenance task. Normally your partner would require a Point to Site VPN to the System, Terminal Server access and someone from your team would need to enable users anytime they want to access.
With Azure Bastion, you would only grant access based on the task of the partner. Let’s take a look at the workflow.
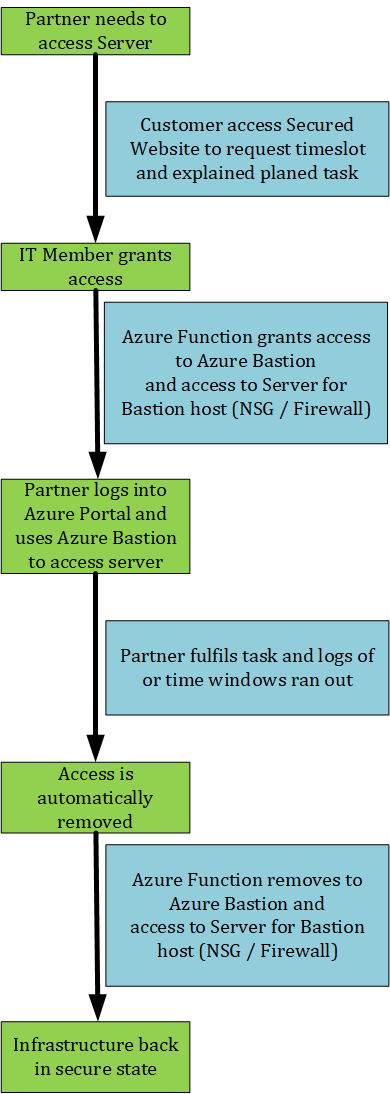
As you can see, it’s pretty simple to use Azure Bastion together with some other components to simply improve your security and cooperation with partners.
Here you can find some more documentation to create those functions and security options.
Azure Functions networking options | Microsoft Docs
Assign Azure roles using Azure PowerShell – Azure RBAC | Microsoft Docs
In the next use case, we will look into encapsulated environments.
Encapsulated environment
Did you ever work in a fully encapsulated Azure Environment which has only extremely limited access to the outside world like only via Frontend Systems using HTTPs port 443 and no access to the backend?
Often those environments do not have any access using VPN or other access to backend systems.
In those scenarios, Azure Bastion can help because you do not need any additional access except to the Azure Portal. From the Azure Portal, you can start a secured session and access the backend without any additional external ports opened.
Often the encapsulated environments are combined with a Just enough and Just in Time Administration strategy.
Here the Azure Bastion usage simplifies the administration, and it keeps a highly secured environmental status.
Alternatives
Did you know that there are alternatives to Azure Bastion that give you more options in regards to tooling and web access?
Windows Admin Center on Virtual Machine in Azure
One alternative is running Windows Admin Center on a Windows Virtual Machine on Azure.
Windows Admin Center Overview | Microsoft Docs
With Windows Admin Center you can administrate Windows and Windows Server from a Web Interface which can be put behind an Azure Public Loadbalancer, Traffic Manager or Web Application Firewall or Frontdoor. It can be integrated into Azure Active Directory to enable Conditional Access and Muli Factor Authentication.
You can add different plugins to admin your different Windows Server Features and Roles or your clients without using RDP to access the servers. If you need additional tools, you can install them on the server too. If you for example need to access a server using SSH or SQL Client, you can open the Windows Admin Center and use the Web Interface to start an HTTPs/RDP Session to the Windows Admin Center Server. Afterwards, you can just start the tool or session.
I prefer to use an Azure B-Series Virtual Machine Size to host the Windows Admin Center. B – Series Virtual Machines are burstable Virtual Machines running on a low level until they are used. They have a very low price point and the use cases with Windows Admin Center makes them an effective alternative to Azure Bastion Service.
B-series burstable – Azure Virtual Machines | Microsoft Docs

Azure Windows Admin Center in Azure Portal
Azure Windows Admin Center in Azure Portal is basically the same solution as Admin Center but focuses on the administration of Windows Virtual Machines in Azure. It gives you access to the Windows Virtual Machine functions and operations without installing Windows Admin Center but you cannot install additional tools except those included in Windows Admin Center and it cannot be used for Linux. You can find more information here.
Use Windows Admin Center in the Azure portal to manage a Windows Server VM | Microsoft Docs
How to Set Up Azure Bastion
You can add Azure Bastion to any existing Virtual Network, but you need to be able to add another /26 Subnet dedicated to Bastion to the Virtual Network. If you don’t have that space left, you need to add an additional address space to the Virtual Network.
The screenshot below shows how to add an address space to the subnet. To add an address space to a Virtual Network, you need to remove the Virtual Network Peering first.
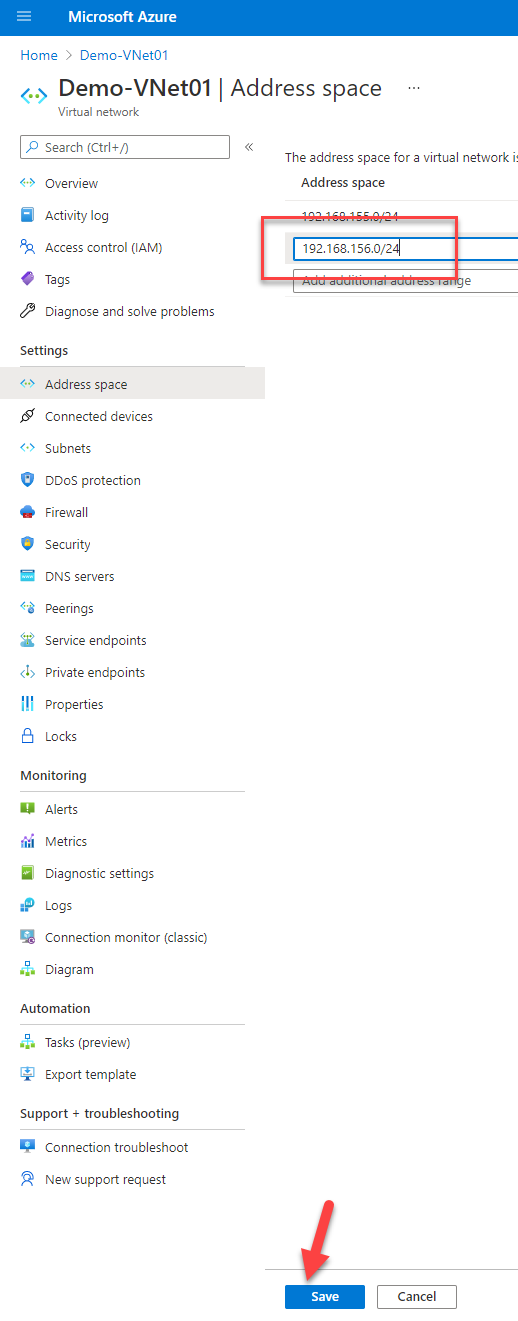
The following guide explains how to deploy Azure Bastion to connect to a Virtual Machine.
Tutorial: Create an Azure Bastion host: Windows VM: portal | Microsoft Docs
When Should I use Azure Bastion?
The following table should provide an overview of when you should use Azure Bastion and when you should use a traditional Jump Box.
| Use Case | Azure Bastion | Jump Box | Azure Windows Admin Center |
| Simple integration into JIT And JEA |
++ |
+ |
+ |
| Highly available out of the box |
++ |
– |
+ |
| Integrated in RBAC |
++ |
– |
+ |
| Cost efficient when 24/7 used |
– |
+ |
++ |
| Tools can be installed |
– |
++ |
+ (Admin Center Only) |
| Flexibility for other tasks |
– |
++ |
+ |
| User Management using Azure AD |
++ |
+ |
+ |
| Accessible using Azure Portal |
++ |
– |
++ |
| Additional admin work like backup needed |
++ |
— |
++ |
| Accessing via RDP and SSP |
++ |
+ (RDP only) |
+ (RDP only) |
| Can Access Windows and Linux |
++ |
+ (via tools on host) |
– |
Limitations of Azure Bastion
Azure Bastion Service is a great tool to improve security. As it is a very limited service only acting as HTTPs to RDP/SSH proxy, it sometimes easily reaches limitations in administrative tasks, especially if you need special tools.
If you reach the limitations of Azure Bastion Services, there are alternatives out there, that help you keep the same security standards and improve the toolbox you may need. But please be aware that those alternatives can improve your administrative efforts.
Always try to balance your needs and do not tend to a solution because it looks great on a sales paper. Tools like Azure Bastion and Virtual Machines are Azure Consumer Revenue-based or free of charge like Windows Admin Center. So you can try which solutions works best in your daily tasks and routines.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









