Save to My DOJO
As I was tinkering with a few things in Azure virtual WAN, I thought it would be a great idea to write a short guide on how to connect Site 2 Site VPN Device to virtual WAN which is not a managed CPE Partner.
After a conversation with Andy Syrewicze, we decided to show you how to perform the configuration using a Ubiquiti Dream Machine Pro. This guide also applies to the below Ubiquiti Products, but it also gives you a framework that is applicable to other vendors such as Sophos or LanCom:
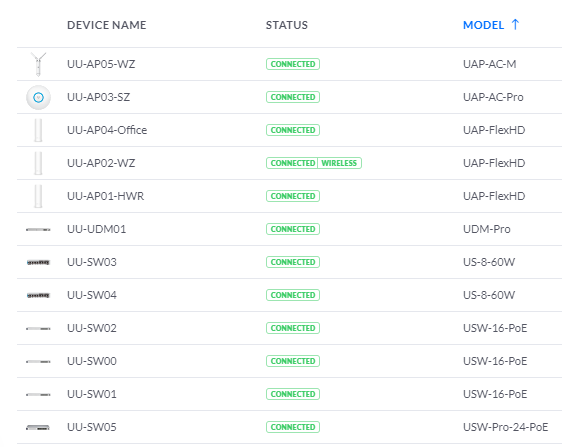
There are two reasons why we decided on the Ubiquiti. First, the devices are kind of tricky when it comes to VPN to Azure, and second, we both are Ubiquiti Fans and have huge installations at home. You can see my installation in the screenshot below:
Prepare Azure Virtual WAN
Let us first prepare our Virtual WAN to function as a VPN endpoint. To do so, you need to deploy a virtual WAN Hub with a VPN Gateway in it.
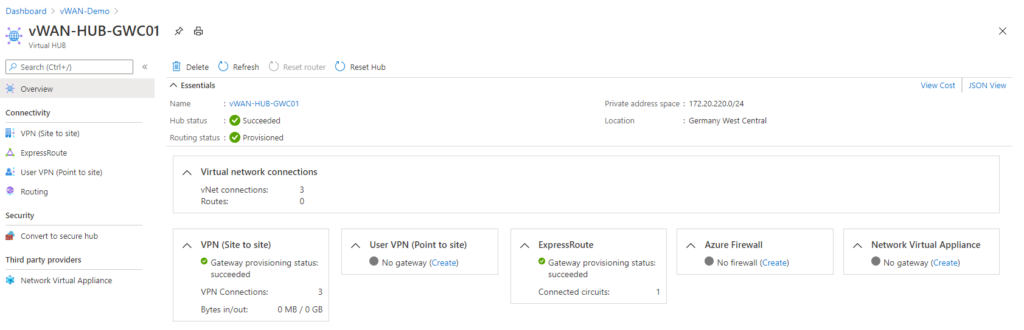
To deploy the Hub, I followed standard Microsoft deployment guides provided below.
After I configured the hub, I started to configure the VPN Site for my location.
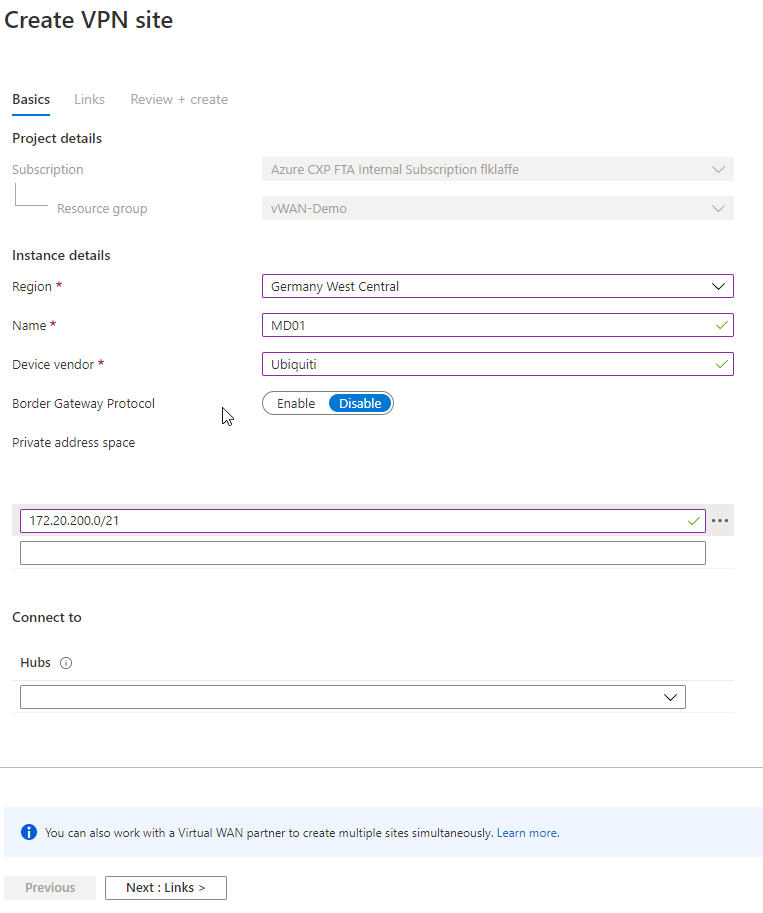
In my case, I left BGP disabled because the UDN Pro does not support Border Gateways Protocol. If you use a Ubiquiti Edge, BGP enabled VPN Device like von Juniper or are ok with using a Ubiquiti Security Gateway CLI configuration, you can enable BGP.
- EdgeRouter – Border Gateway Protocol (BGP) – Ubiquiti Support and Help Center
- Connect Ubiquiti USG to Azure VWAN Gateway using BGP | Crazy Cloud Ideas (sameeraman.github.io)
I left the Connect to Hubs option empty because it would use the default VPN configuration. In our case, we will use a custom and more stable configuration later on.
Now I configured the WAN Links. In a classic Azure Gateway configuration, that would be the local gateway IP.
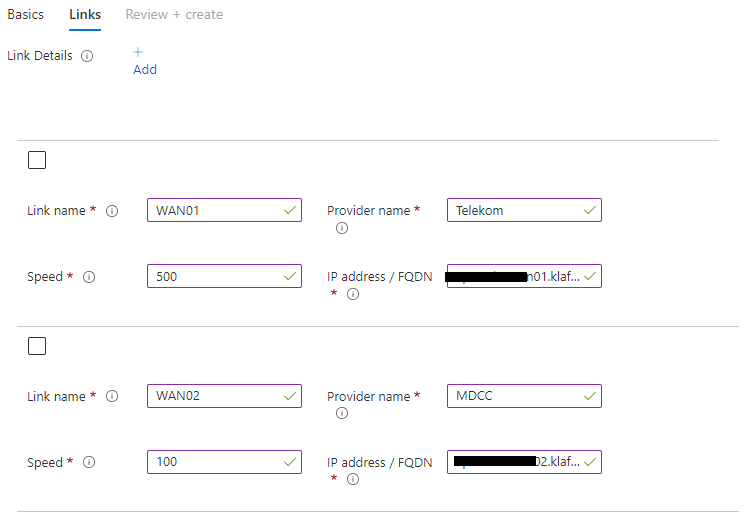
In my example configuration, I made two changes to a traditional setup. The first change is that I use two WAN links, I currently have two Internet Service Providers (ISPs) for internet redundancy and connectivity to Azure. So it makes sense to configure both of them to link to my virtual WAN Gateway. The other change is that I use the Frequently Asked Domain Name (FQDN). That gives me the option to use dynamic DNS (DDNS) Services or a self-made DDNS.
In my case, I use a self-made one and host the DNS entries for my VPN in Azure DNS.
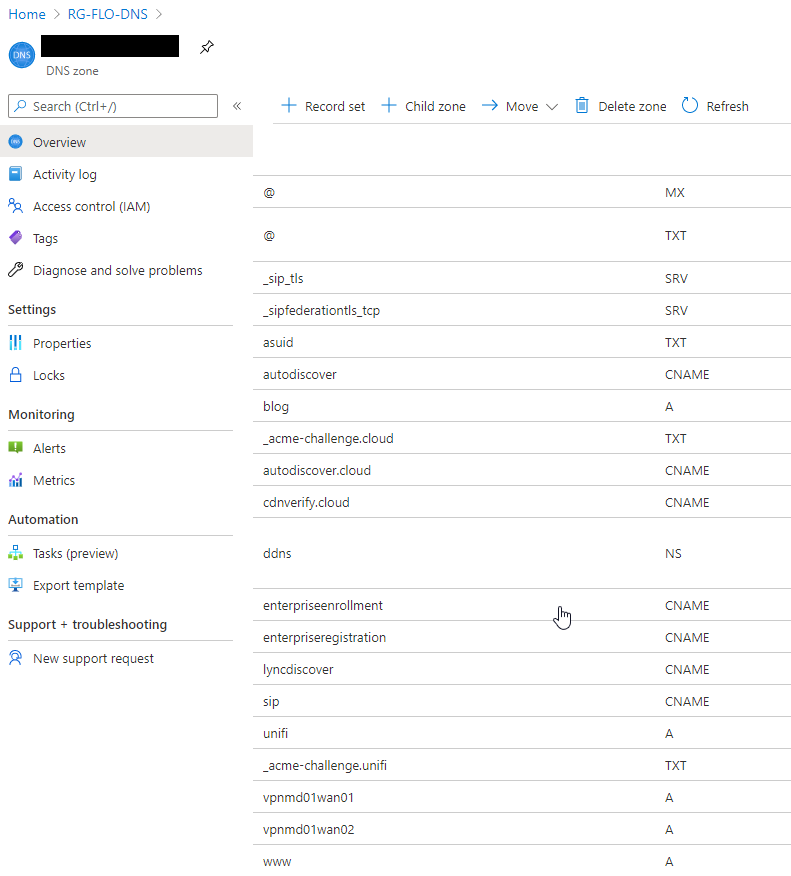
For the DDNS Service, I leveraged the code provided by cirrius tech. Create your own Dynamic DNS service using Azure DNS – part 1 (cirriustech.co.uk)
After your configuration of the links is done, Azure virtual WAN will run a validation of your configuration.
As soon as you passed the validation, you can create the new VPN Site.
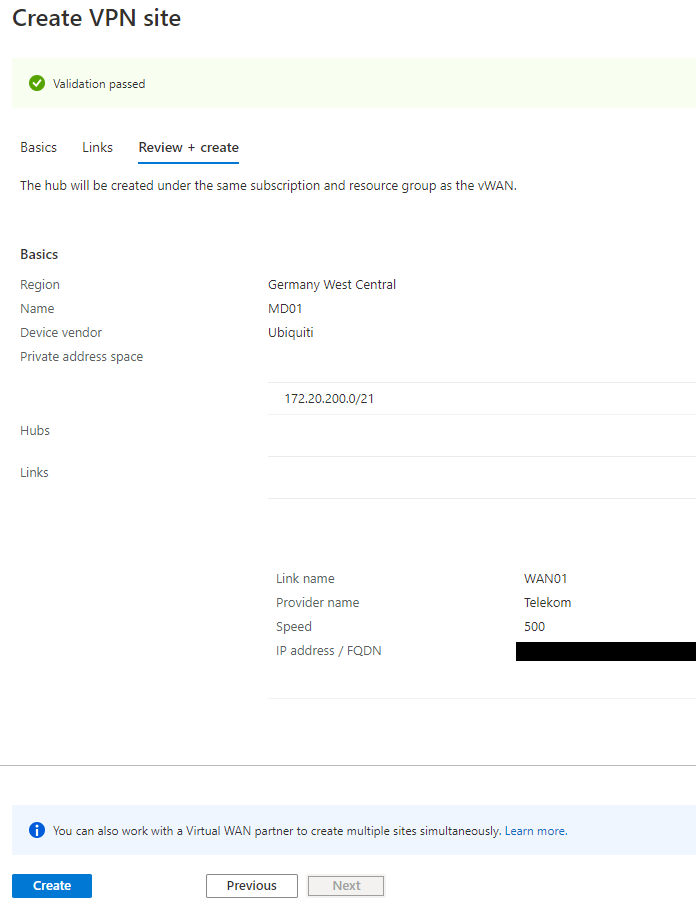
After the VPN Site is deployed, we can start configuring the Hub connection and VPN IPSec Policies.
Configure Hub and IPSec
Now we navigate to the hub where we want to connect the VPN Site to and click on VPN Site.
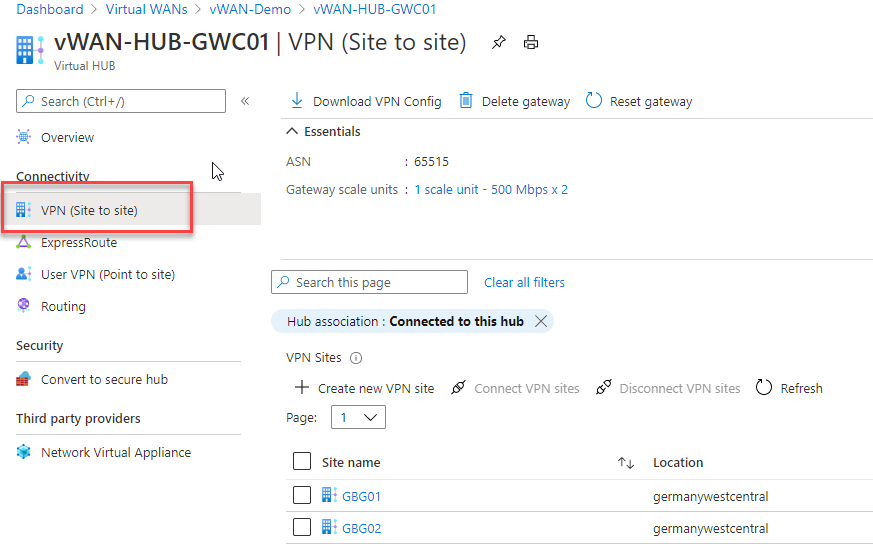
You will not see your VPN Site in the first place because virtual WAN has a pretty annoying default filter, The filter only shows connected sites. Just remove the filter.
After you removed the filter, the VPN Site will show up.
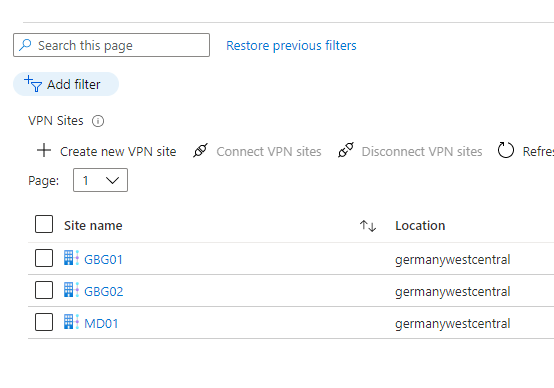
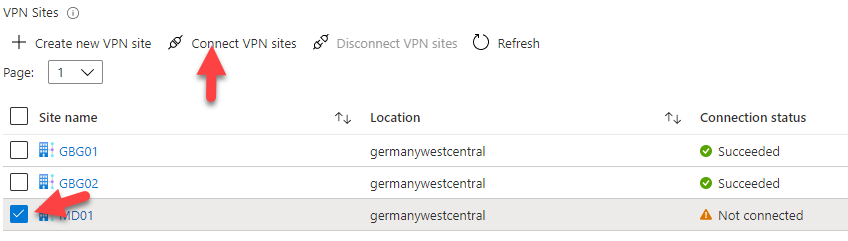
Now let’s connect our site to the hub. To do so, please select the site and click connect.
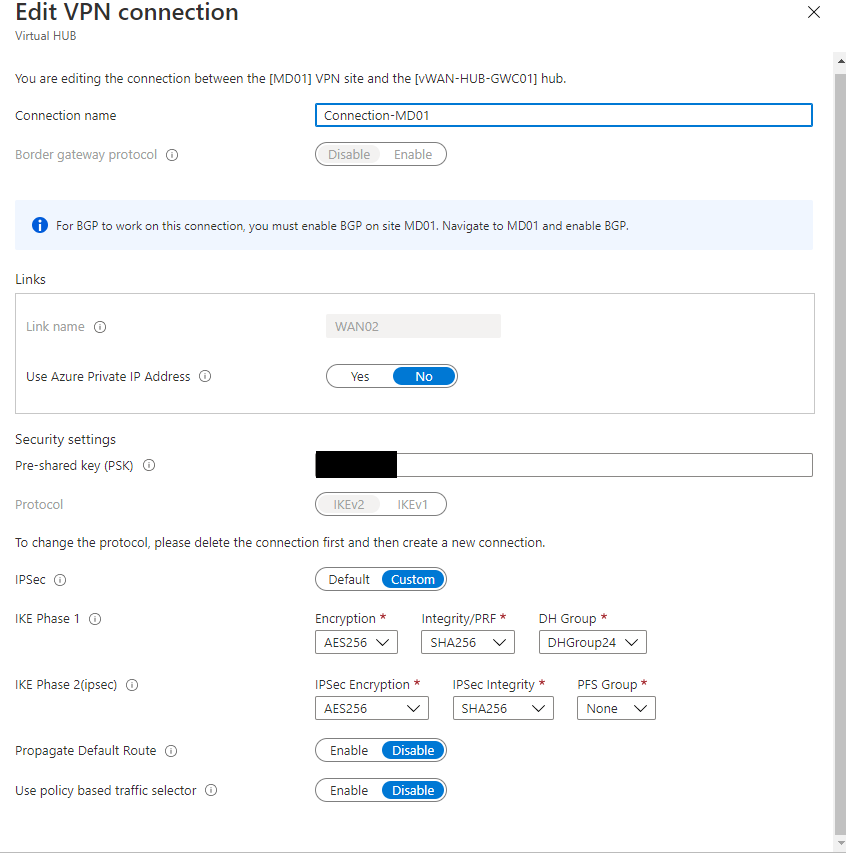
The configuration blade will show up. I used a custom configuration which wors well with the Ubiquiti devices. You can also use the default configuration but then you need to change the DH Group in the Ubiquiti from 2 to 24 and you only use lower encryption standards. That is why I prefer my custom configuration.
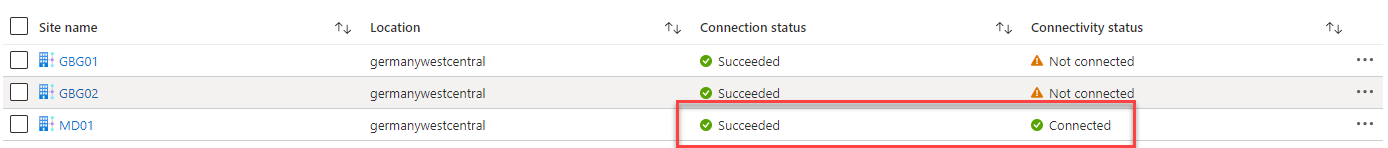
After a successful configuration, you should see the connection status as succeeded and the connectivity status as updating.
Within the next step, we will prepare the Ubiquiti VPN Device and configuration.
Prepare Ubiquiti VPN Device
Before we start the configuration, we need to collect some information from Azure to add them later to you Ubiquiti tunnel configuration.
First, we need public IPs from the Azure Gateways. There are different options to do that.
The classic one is to download the VPN configuration file.
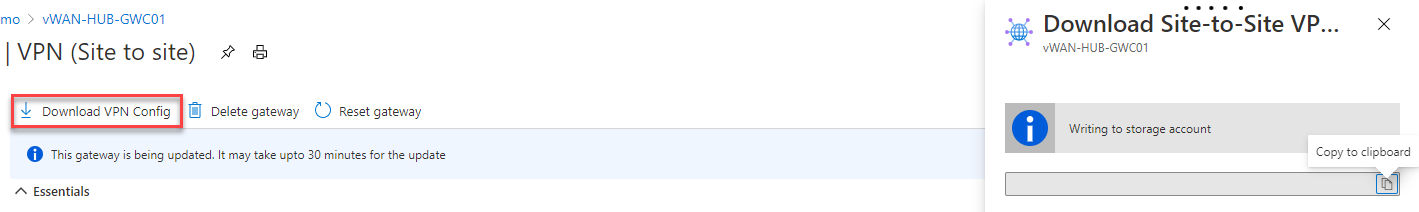
Here you will find all the necessary information for the configuration.
[
{"configurationVersion":{"LastUpdatedTime":"2021-01-27T13:39:28.0925596Z","Version":"eb76d019-4242-443a-a1d9-d56a346972b9"},"vpnSiteConfiguration":{"Name":"GBG01","IPAddress":"","LinkName":"WAN01","Office365Policy":{"BreakOutCategories":{"Optimize":false,"Allow":false,"Default":false}}},"vpnSiteConnections":[{"hubConfiguration":{"AddressSpace":"172.20.220.0/24","Region":"Germany West Central","ConnectedSubnets":["10.0.0.0/24","10.0.1.0/24","192.168.155.0/24","192.168.22.0/24"]},"gatewayConfiguration":{"IpAddresses":{"Instance0":"","Instance1":""}},"connectionConfiguration":{"IsBgpEnabled":false,"PSK":"","IPsecParameters":{"SADataSizeInKilobytes":102400000,"SALifeTimeInSeconds":3600}}}]},
{"configurationVersion":{"LastUpdatedTime":"2021-01-27T13:39:28.0925596Z","Version":"4d0dabe5-d5b1-4fc2-8a77-68fc7cdff159"},"vpnSiteConfiguration":{"Name":"MD01","IPAddress":"","LinkName":"WAN02","Office365Policy":{"BreakOutCategories":{"Optimize":false,"Allow":false,"Default":false}}},"vpnSiteConnections":[{"hubConfiguration":{"AddressSpace":"172.20.220.0/24","Region":"Germany West Central","ConnectedSubnets":["10.0.0.0/24","10.0.1.0/24","192.168.155.0/24","192.168.22.0/24"]},"gatewayConfiguration":{"IpAddresses":{"Instance0":"","Instance1":""}},"connectionConfiguration":{"IsBgpEnabled":false,"PSK":"","IPsecParameters":{"IpsecEncryption":"AES256","IpsecIntegrity":"SHA256","IkeEncryption":"AES256","IkeIntegrity":"SHA256","PfsGroup":"None","DhGroup":"DHGroup24","SADataSizeInKilobytes":102400000,"SALifeTimeInSeconds":27000}}}]},
{"configurationVersion":{"LastUpdatedTime":"2021-01-27T13:39:28.0925596Z","Version":"b3819f84-df07-4577-b657-6bf5efebcede"},"vpnSiteConfiguration":{"Name":"MD01","IPAddress":"","LinkName":"WAN01","Office365Policy":{"BreakOutCategories":{"Optimize":false,"Allow":false,"Default":false}}},"vpnSiteConnections":[{"hubConfiguration":{"AddressSpace":"172.20.220.0/24","Region":"Germany West Central","ConnectedSubnets":["10.0.0.0/24","10.0.1.0/24","192.168.155.0/24","192.168.22.0/24"]},"gatewayConfiguration":{"IpAddresses":{"Instance0":"","Instance1":""}},"connectionConfiguration":{"IsBgpEnabled":false,"PSK":"","IPsecParameters":{"IpsecEncryption":"AES256","IpsecIntegrity":"SHA256","IkeEncryption":"AES256","IkeIntegrity":"SHA256","PfsGroup":"None","DhGroup":"DHGroup24","SADataSizeInKilobytes":102400000,"SALifeTimeInSeconds":27000}}}]},
{"configurationVersion":{"LastUpdatedTime":"2021-01-27T13:39:28.0925596Z","Version":"7b6a0635-7229-451e-82e1-532ae86a109a"},"vpnSiteConfiguration":{"Name":"GBG02","IPAddress":"","LinkName":"WAN01","Office365Policy":{"BreakOutCategories":{"Optimize":false,"Allow":false,"Default":false}}},"vpnSiteConnections":[{"hubConfiguration":{"AddressSpace":"172.20.220.0/24","Region":"Germany West Central","ConnectedSubnets":["10.0.0.0/24","10.0.1.0/24","192.168.155.0/24","192.168.22.0/24"]},"gatewayConfiguration":{"IpAddresses":{"Instance0":"","Instance1":""}},"connectionConfiguration":{"IsBgpEnabled":false,"PSK":"","IPsecParameters":{"SADataSizeInKilobytes":102400000,"SALifeTimeInSeconds":3600}}}]}
]
The important points in that file are.
- “hubConfiguration”:{“AddressSpace”: – shows you the IP Subnet used for the hub
- “ConnectedSubnets” – shows you the IP Subnet of the connect virtual networks
- “IpAddresses”:{“Instance0″:””,”Instance1″:”” – shows you the public IP of the Azure Loabbalancers which are connected to the Azure Virtual WAN VPN Gateways
You can also collect this information manually by looking into the Gateway configuration, which came with a release in Q3 2020.
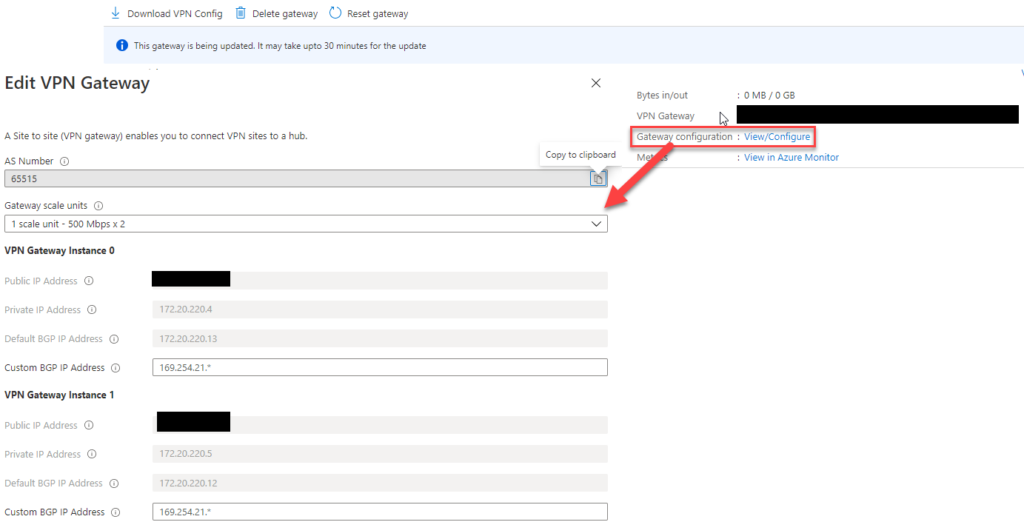
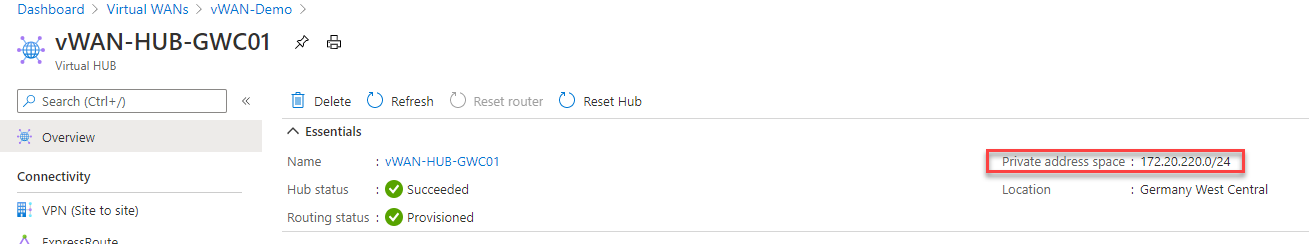
To collect the Hub IP Subnet you need to go back to the virtual WAN Hub overview screen.
To find the connected VNet IP spaces, you need to go to the connected VNet list in the main hub overview and then click on every single VNet to find the details.
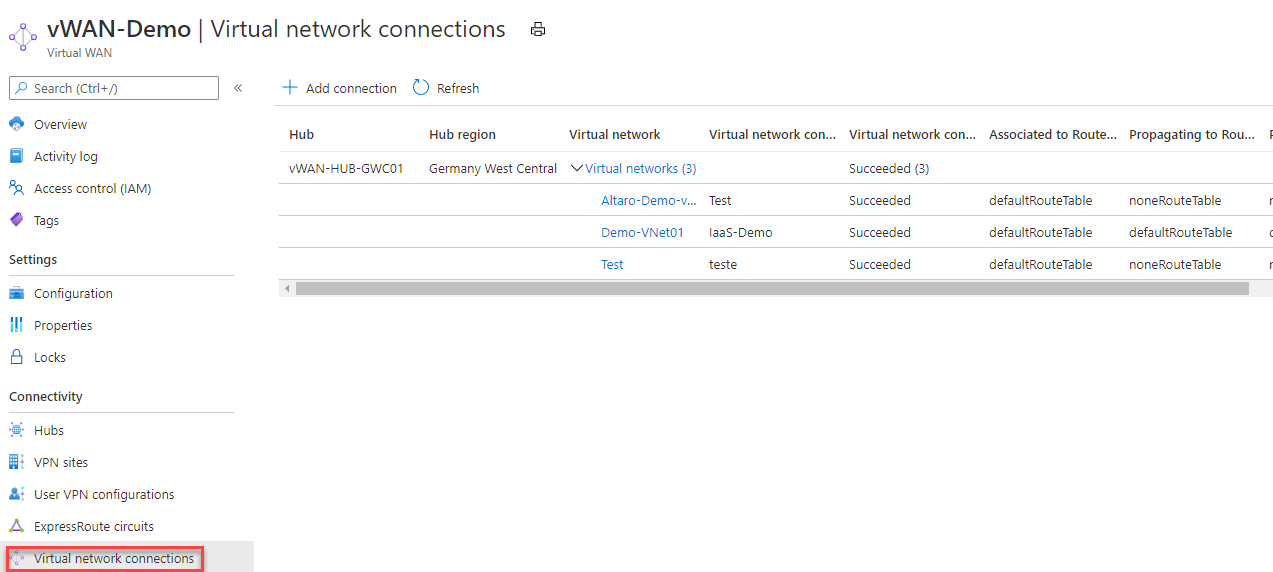
As you can imagine, that is a very uncomfortable way to collect the information. So I would suggest staying with the VPN Config file. Now let us start with the configuration of our Ubiquiti VPN Device.
VPN Device configuration
To be honest, for my configuration and management, I use the new Ubiquiti Alpha UI. It has some feature available which are not enabled in the classic UI and it also has removed a bug with Azure VPN tunnels in regards to disabling dynamic routing and PFS. To switch to Alpha UI, you need to go to the System Menu of you controller and switch to beta features.
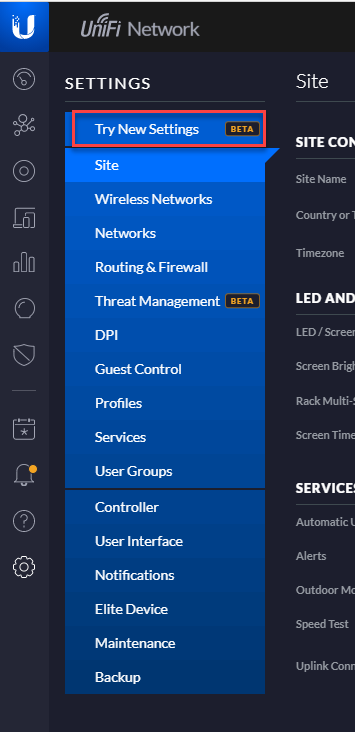
Navigate to Networks and create a new one.
Now you can add a Site 2 Site VPN and configure it as we did on the Azure Site.
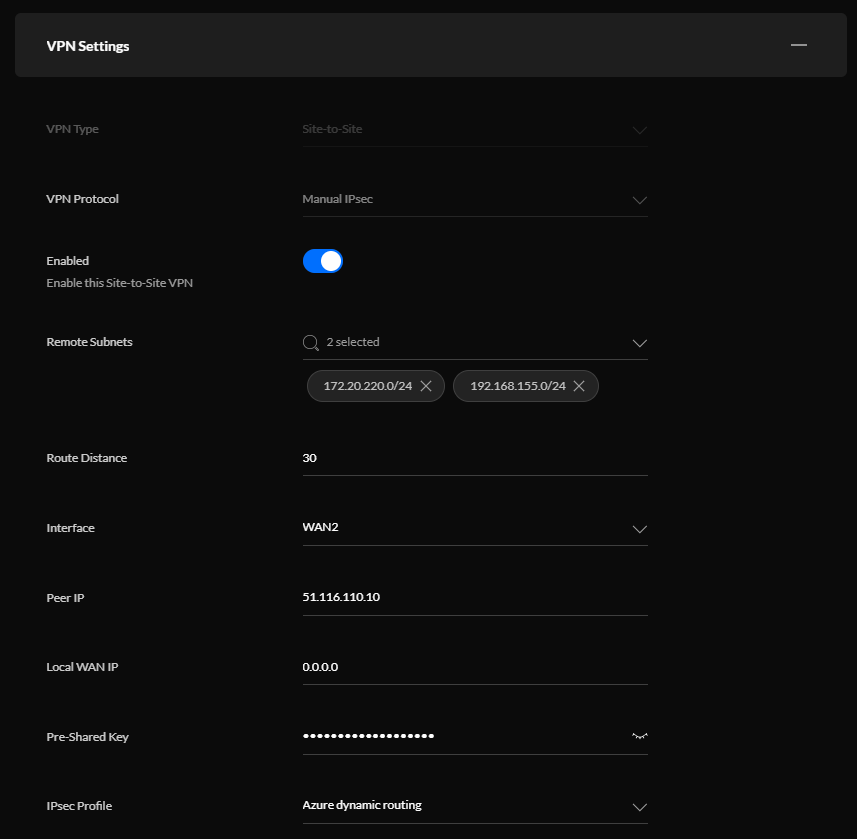
The following points in VPN Settings are important to know:
- Interface: You need to choose the Interface where you want to connect your tunnel from. In my case, I will use my backup connection instead of my primary internet connection.
- Peer IP: here you add the public IP of virtual WAN Instance 0 or 1
- Local WAN IP: in case you have a static public IP, you should add that public IP here. If you use a dynamic IP or dynamic DNS, you add 0.0.0.0 as you local WAN IP
- IPSec Profile: set to dynamic routing
Now we need to configure the IPSec policy.
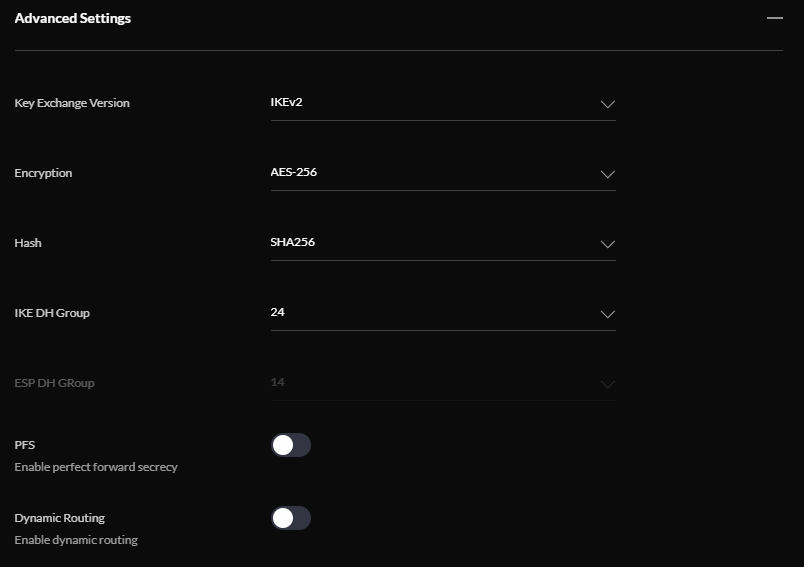
I prefer to run a static configuration to later change the routing and only allow some of my network to connect to Azure but a dynamic routing configuration also works pretty well.
As soon as you configured the VPN Settings on the Ubiquiti it should take around 5 minutes until the tunnel comes up.
Closing
Thank you for reading through the article. I hope it was helpful for all of you. If you need more details or have additional questions, please feel free to leave me a comment.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!










91 thoughts on "How to configure Azure virtual WAN VPN Site-2-Site with unmanaged VPN device"
thank you for contribute
Thanks for this config. Agree Unifi device to Azure isn’t always straightforward.
As I hear from my contacts, there is a firmware for UCS and UDM coming, that should fix some issues. I would really like to see ubiquiti integrate in vWAN and offering Dynamic DNS integration for generic providers. That would help to leverage the FQDN Feature. A friend of mine and me currently try to get an Azure DNS based dynamic DNS for UBNT up and running but there are still a lot of issues. 🙁